Mozilla Reduces Threat of Export-Grade Crypto to Firefox article tells that Logjam was one of several downgrade attacks discovered in the last 18 months that could theoretically allow a resourced attacker to take advantage of lingering export-grade cryptography to read and modify data over a supposedly secure connection. Other related recent crypto problems are recent OpenSSL critical bug fix, FREAK attack and earlier problems like Heartbleed etc..
Mozilla Reduces Threat of Export-Grade Crypto to Firefox article says that Mozilla last week took new steps to protect against Logjam in the Firefox browser to deny connections to servers using weak Diffie-Hellman (algorithm is used in symmetric encryption ciphers such as AES to set up key exchanges) keys. To get idea is works, check out this example using paint colors From: Diffie–Hellman key exchange.
This is not the first time something has been done against Logjam attack – all major browser makers (including Mozilla) had released fixes to their browsers already in 2015. But always some more can be done. Now Mozilla is increasing the minimum key size to 1023 bits for TLS handshakes configured to use the Diffie-Hellman key exchange. The disadvantage of this change is that a small number of servers are not configured to use strong enough keys, and users trying to connect them will get error messages. The recommendation for developers: If you have a web or mail server, you should disable support for export cipher suites and use a 2048-bit Diffie-Hellman group. If you are application developers, write applications so that they reject Diffie-Hellman primes smaller than 1024-bit (like Mozilla just did).
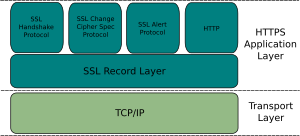
There is also another vulnerability on the wild: Millions of HTTPS, SSH, and VPN servers all use the same prime numbers for Diffie-Hellman key exchange. The most efficient algorithm for breaking a Diffie-Hellman connection—is dependent only on this prime. Why is it the case that so many services are using precisely the same primes in implementing Diffie-Hellman key exchange? It was though that it would take a computer ages to crack your secret numbers, but since everyone got lazy and stuck to using the same keys for an DH exchange, you can use tables to help to crack the secrets.
For more details on those attacks check out Weak Diffie-Hellman and the Logjam Attack web page.
ogjam was one of several downgrade attacks discovered in the last 18 months that could theoretically allow a resourced attacker to take advantage of lingering export-grade cryptography to read and modify data over a supposedly secure connection.
See more at: Mozilla Reduces Threat of Export-Grade Crypto to Firefox https://wp.me/p3AjUX-vua
Logjam was one of several downgrade attacks discovered in the last 18 months that could theoretically allow a resourced attacker to take advantage of lingering export-grade cryptography to read and modify data over a supposedly secure connection.
See more at: Mozilla Reduces Threat of Export-Grade Crypto to Firefox https://wp.me/p3AjUX-vua
Logjam was one of several downgrade attacks discovered in the last 18 months that could theoretically allow a resourced attacker to take advantage of lingering export-grade cryptography to read and modify data over a supposedly secure connection.
See more at: Mozilla Reduces Threat of Export-Grade Crypto to Firefox https://wp.me/p3AjUX-vua
0 Comments
Be the first to post a comment.