I’m Being Followed: How Google—and 104 Other Companies—Are Tracking Me on the Web is a voyage into the invisible business that funds the web. Who are these companies and what do they want from me? Even if you’re generally familiar with the idea of data collection for targeted advertising, the number and variety of these data collectors will probably astonish you. Right now, a huge chunk of what you’ve ever looked at on the Internet is sitting in databases all across the world.
Many different companies want to know as much about me and what’s on my screen as they possibly can, although they have different reasons for their interest. To be clear, these companies gather data without attaching it to your name (most of the companies do not know names of the people they are following); they use that data to show you ads you’re statistically more likely to click. That’s the game, and there is substantial money in it. Some of the best minds of my generation are thinking about how to make people click ads (think for example how many highly talented people Google has). The online advertising industry argues that technology is changing so rapidly that regulation is not the answer to queasiness about all that data going off to who-knows-where.
The bad news is that people haven’t taken control of the data that’s being collected and traded about them. At the moment there is a fascinating scrum over what “Do Not Track” tools should do and what orders websites will have to respect from users. Do Not Track signals a user’s opt-out preference with an HTTP header. Several large third parties have already committed to honor Do Not Track, but many more have been recalcitrant.
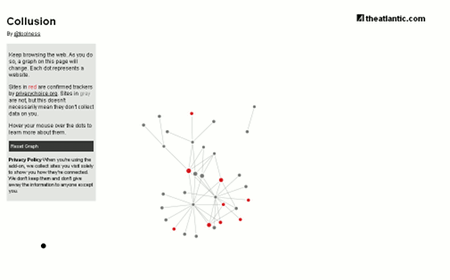
It’s now time for us to watch the watchers. Track Who’s Tracking You With Mozilla Collusion. Collusion is a Firefox browser add-on that lets you track who’s tracking you across the web for behavioral targeting purposes. There is a demonstration put up at collusion.toolness.org, which takes you through five popular websites and visualizes the data collection companies that track you across them. From there, you can download the add-on if you want to see the tracking visualization of your own browsing behavior evolve in real-time.
Collusion looks to offer more transparency to users by creating a visualization of how your data is being spread to different companies as you navigate the web. Each time it detects data being sent to a behavioral tracker, it creates a red (advertisers), grey (websites) or blue dot on the visualization and shows the links between the sites you visit and the trackers they work with. Mozilla has created an online demo to show just how quickly your data ends up in the hands of dozens of different companies as you move on popular web popular sites.
If you need the source code, it’s all at github.com/toolness/collusion. For some more details take a look at Toolness Blog posting on Collusion. This is an interesting experiment to track on who is tracking you. Collusion is about alerting users to tracking that’s happening without their consent. Very interesting! The more access to metrics the better.
240 Comments
Tomi Engdahl says:
Acxiom exposed: A peek inside one of the world’s largest data brokers
http://www.itworld.com/it-management/356637/acxiom-exposed-peek-inside-one-world-s-largest-data-brokers
Acxiom knows where you live, where you shop and what you like to do. But it’s not quite the evil data monolith you might expect.
Acxiom is one of the largest data brokers in the world, yet few average consumers know much about it. You’re about to find out a bit more. But before I get into that I’d like to correct two errors related to Acxiom that appeared recently in TY4NS.
Most people know the company as a data broker. Some people know it as an online tracking company. But very few know that Acxiom is also an IT services firm. Given that it’s been gathering data about hundreds of millions of consumers since 1969, storing it on banks of mainframes at its headquarters in Little Rock and elsewhere, that shouldn’t be surprising. According to Gartner, Acxiom is one of the top three mainframe outsource providers in North America.
As of last month, Acxiom is also a cloud services provider. Its PrivateCloud aims to offer secure mainframe computing services for enterprises in the $200 million to $2 billion range, says Acxiom Cloud Leader Jesse Luna.
Data be the day
When it comes to data, Acxiom has two core businesses, Glasgow explained. One revolves around risk management; companies hire Acxiom to verify that people are in fact who they claim to be. The other collects data from a wide range of sources to build personally identifiable profiles which they then rent to marketers.
So where does all this information come from? I wanted to know. For marketing data Acxiom draws from three primary sources, Glasgow explained. One is public records, such as property ownership or professional licenses. The second is consumer surveys, magazine subscriber lists, catalogs, and warranty cards. The third category is summary reports about retail purchases.
“People often have the wrong idea about the type of data we collect or how granular it is,” she says. “We don’t know that you bought a blue shirt from Lands End. We just know the kinds of products you are interested in. We’re trying to get a reasonably complete picture of your household and what the individuals who live there like to do.”
Does Acxiom collect data from supermarket loyalty cards, I asked? No. Banking data or airline frequent flyer programs? No. Facebook and Twitter? No. Despite the fact social networks are largely public information, Acxiom doesn’t use them as a source.
For the last few years Acxiom has also been active in the online tracking space. But here too, Glasgow says most people misunderstand how Acxiom uses your data. When you visit a Web site that deposits an Acxiom cookie, it will request data about your offline interests and activities to “enhance” the profile it has of you.
But it will only request this data if the site already knows who you are – ie, you’ve logged in.
Privacy: Still ticking
With all of the doom and gloom about privacy lately, I asked Glasgow if she was optimistic about the future of privacy.
“When I started in the early 1990s there were no restrictions at all to speak of,” she says. “We still collected a lot of data, but it was all fair game. Companies like ours that collected data realized many years ago we have a responsibility that comes with playing in this space, so we put a lot of self governance in place.”
Starting in the 2000s, we began to see more laws spelling out what people can and can’t do with data – mostly in Canada, Europe, and Asia. While they don’t have legal force here in the States, they do provide companies with guidelines for acceptable behavior, she says.
Tomi Engdahl says:
In Bloomberg Uproar, Ethics Flags For New Media
http://www.huffingtonpost.com/2013/05/16/in-bloomberg-uproar-ethi_n_3284025.html
Now, a byproduct of Bloomberg’s widely admired and novel business model has ensnared his company in a problem of its own making. But the uproar — revolving around specialized computer terminals unknown to most news consumers, and the reporters who tapped into data showing how high-powered Wall Street customers were using them — is potentially about much more than Bloomberg.
In practice, it has become clear, that meant giving Bloomberg journalists access to data about individual customers’ terminal usage, a practice that progressed from mere service-mindedness to keeping tabs on clients’ habits for reporting purposes.
Bloomberg LP, which started as a provider of sophisticated financial data to bond traders and only later expanded to include a journalistic enterprise, has few direct parallels in media.
Tomi Engdahl says:
Mozilla needs more time to work on it’s Cookie following protection to work well:
C is for Cookie
https://brendaneich.com/2013/05/c-is-for-cookie/
Mozilla is engaged in a broad, deep conversation about Internet privacy. We believe in putting users in control of their online experience, and we want a healthy, thriving web ecosystem — we do not see a contradiction. However, sometimes a crucial experiment is required to prove it.
The idea is that if you have not visited a site (including the one to which you are navigating currently) and it wants to put a cookie on your computer, the site is likely not one you have heard of or have any relationship with. But this is only likely, not always true. Two problems arise:
False positives.
False negatives.
Our challenge is to find a way to address these sorts of cases. We are looking for more granularity than deciding automatically and exclusively based upon whether you visit a site or not, although that is often a good place to start the decision process.
We plan to ship an evolution of the patch “on” by default, but we want to make refinements first. To make sure we get this right we need more data. Our next engineering task is to add privacy-preserving code to measure how the patch affects real websites.
There are many conflicting claims about how this patch will affect the Internet.
The patch has progressed to the Beta release channel for Firefox 22, but it is not “on” by default there. This allows more people to test the patch via Firefox’s “preferences”
The patch remains in the Aurora channel for Firefox, where it is “on” by default.
Tomi Engdahl says:
Why Google Will Crush Nielsen
http://www.mondaynote.com/2013/05/19/why-google-will-crush-nielsen/
Internet measurement techniques need a complete overhaul. New ways have emerged, potentially displacing older panel-based technologies. This will make it hard for incumbent players to stay in the game.
The web user is the most watched consumer ever. For tracking purposes, every large site drops literally dozens of cookies in the visitor’s browser. In the most comprehensive investigation on the matter, The Wall Street Journal found that each of the 50 largest web sites in the United Sates, weighing 40% of the US page views, installed an average of 64 files on a user device.
But when it comes to measuring a digital viewer’s commercial value, sites rely on old-fashioned panels, that is limited user population samples. Why?
Panels are inherited. They go back to the old days of broadcast radio
Nielsen Company made a clever decision: they installed a monitoring box in 1000 American homes. Twenty years later, Nielsen did the same, on a much larger scale, with broadcast television.
Publishers monitor the pulse of their digital properties on a permanent basis. In most newsrooms, Chartbeat (also imperfect, sometimes) displays the performance of every piece of content, and home pages get adjusted accordingly.
The developing field of statistical pairing technology shows great promise. It is now possible to pinpoint a single user browsing the web with different devices in a very reliable manner.
Over time, your digital fingerprint will become more and more precise. Until then, the set of four cookies is independent from each other. But the analytics firm compiles all the patterns in single place. By data-mining them, analysts will determine the probability that a cookie dropped in a mobile application, a desktop browser or a mobile web site belongs to the same individual.
Obviously, Google is best positioned to perform this task on a large scale. First, its Google Analytics tool is deployed over 100 millions web sites. And the Google Ad Planner, even in its public version, already offers a precise view of the performance of many sites in the world.
Tomi Engdahl says:
SAP touts service that sells customer data from phone firms
http://news.cnet.com/8301-1009_3-57585627-83/sap-touts-service-that-sells-customer-data-from-phone-firms/
The European maker of enterprise software would serve as a kind of middleman, analyzing data gathered by various wireless operators, selling results to marketers, and sharing the profits with the wireless companies.
Verizon Wireless already sells its customers’ mobile data to marketers. Now European enterprise-software giant SAP is taking things a step further by testing a service that will sell data collected by a number of wireless providers.
SAP announced its Consumer Insight 365 mobile service this week at the CTIA 2013 wireless show in Las Vegas. The service will, the company said in a release, pull data from SAP’s “extensive partner network” including “over 990 mobile operators;” aggregate and analyze it “without drilling down into user-specific information;” and make results available to subscribers through a Web portal.
SAP says its Mobile Services division works with more than 990 operators and 5.8 billion subscribers across 210 countries.
Tomi Engdahl says:
German Official Criticizes Xbox One’s Data Collecting
Kinect’s all-seeing eye rubs Comissioner Peter Schaar the wrong way.
http://www.ign.com/articles/2013/05/28/german-privacy-official-xbox-one-is-twisted-nightmare
A lot of people were wowed last week when Microsoft showed off the responsiveness of the new generation Kinect perched on top of the forthcoming Xbox One, but not everyone is thrilled by the advances the company has made in facial recognition. Escapist reports that when German website Spiegel asked Germany’s Federal Data Protection Commissioner Peter Schaar about the technology, he called it a “monitoring device.”
“The Xbox continuously records all sorts of personal information about me. Reaction rates, my learning or emotional states,” Schaar said. “They are then processed on an external server, and possibly even passed on to third parties. Whether they will ever deleted, the person cannot influence.”
With Microsoft deliberately keeping things under wraps, folks like Schaar are concerned that more damaging facts are obscured from the public. Most importantly, that information about individual users will filter back to the Seattle-based company’s main data banks, acting a little more Big Brother than most people would be comfortable with.
Tomi Engdahl says:
Yahoo Shuts Down Mail Classic, Forces Switch To New Version That Scans Your Emails To Target Ads
http://techcrunch.com/2013/06/02/yahoo-shuts-down-mail-classic/
Starting the week of June 3rd, tomorrow, Yahoo is discontinuing Mail Classic. It’s requiring all Mail users to switch to the new version of Mail and accept a TOS/Privacy Policy update that lets it scan emails to “deliver product features, relevant advertising, and abuse protection”.
You can opt out of the ads, but if you don’t want to be scanned, you have to ditch Yahoo Mail.
“Yahoo can now openly troll through email for personal information that it can share or hold onto indefinitely.”
Gmail has long scanned your email to show you related ads.
fat loss factor review says:
Great post! We are linking to this particularly great content
on our site. Keep up the great writing.
Tomi Engdahl says:
U.N. Realizes Internet Surveillance Chills Free Speech
http://yro.slashdot.org/story/13/06/04/223225/un-realizes-internet-surveillance-chills-free-speech
“The Electronic Frontier Foundation reports that the United Nations has finally come to the realization that there is a direct relationship between government surveillance online and citizens’ freedom of expression.”
Internet Surveillance and Free Speech: the United Nations Makes the Connection
https://www.eff.org/deeplinks/2013/06/internet-and-surveillance-UN-makes-the-connection
Frank La Rue, the United Nations Special Rapporteur on Freedom of Expression and Opinion delivered this week a landmark report [PDF] on state surveillance and freedom of expression. In preparation, the Special Rapporteur reviewed relevant studies, consulted with experts including EFF, and participated in the state surveillance and human rights workshop
The explosion of online expression we’ve seen in the past decade is now being followed by an explosion of communications surveillance. For many, the Internet and mobile telephony are no longer platforms where private communication is shielded from governments knowing when, where, and with whom a communication has occurred.
The report acknowledges the benefits of technological innovations that have enabled rapid, anonymous, cross-cultural dialogues around the world. Nevertheless, the report warns that these same technologies can open a Pandora’s box of previously unimaginable state surveillance intrusions.
For example, with all the amount of information and evolving surveillance technologies, law enforcement agencies now can:
Directly observe people’s relationships and interactions and make inferences about their intimate and protected relationships.
Examine millions of people’s communications and rapidly identify precise communications interactions on any given topic.
Track any person’s physical movements almost all of the time and draw conclusions about one’s professional, sexual, political, and religious activities, and attitudes from individuals’ associations and Internet traffic.
Routinely retain data for decades, so that statements and interactions can be searched, analyzed, and recalled long after they have been made.
Do all of the above simultaneously.
Tomi Engdahl says:
Report: Verizon providing all call records to U.S. under court order
http://www.washingtonpost.com/world/national-security/verizon-providing-all-call-records-to-us-under-court-order/2013/06/05/98656606-ce47-11e2-8845-d970ccb04497_story.html
The National Security Agency appears to be collecting the telephone records of tens of millions of American customers of Verizon, one of the nation’s largest phone companies, under a top-secret court order issued in April.
The order appears to require a Verizon subsidiary to provide the NSA with daily information on all telephone calls by its customers within the United States and from foreign locations into the United States.
Tomi Engdahl says:
Verizon court order: NSA collecting phone records of millions of Americans daily
http://www.guardian.co.uk/world/2013/jun/06/nsa-phone-records-verizon-court-order
Exclusive: Top secret court order requiring Verizon to hand over all call data shows scale of domestic surveillance under Obama
The order, a copy of which has been obtained by the Guardian, requires Verizon on an “ongoing, daily basis” to give the NSA information on all telephone calls in its systems, both within the US and between the US and other countries.
The secret Foreign Intelligence Surveillance Court (Fisa) granted the order to the FBI on April 25, giving the government unlimited authority to obtain the data for a specified three-month period ending on July 19.
Under the terms of the blanket order, the numbers of both parties on a call are handed over, as is location data, call duration, unique identifiers, and the time and duration of all calls. The contents of the conversation itself are not covered.
Tomi Engdahl says:
Documents: U.S. mining data from 9 leading Internet firms; companies deny knowledge
http://www.washingtonpost.com/investigations/us-intelligence-mining-data-from-nine-us-internet-companies-in-broad-secret-program/2013/06/06/3a0c0da8-cebf-11e2-8845-d970ccb04497_story.html
The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio and video chats, photographs, e-mails, documents, and connection logs that enable analysts to track foreign targets, according to a top-secret document obtained by The Washington Post.
The program, code-named PRISM, has not been made public until now.
there has never been a Google or Facebook before, and it is unlikely that there are richer troves of valuable intelligence than the ones in Silicon Valley.
Equally unusual is the way the NSA extracts what it wants, according to the document: “Collection directly from the servers of these U.S. Service Providers: Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.”
PRISM was launched from the ashes of President George W. Bush’s secret program of warrantless domestic surveillance in 2007, after news media disclosures, lawsuits and the Foreign Intelligence Surveillance Court forced the president to look for new authority.
The court-approved program is focused on foreign communications traffic, which often flows through U.S. servers even when sent from one overseas location to another.
Several companies contacted by The Post said they had no knowledge of the program, did not allow direct government access to their servers and asserted that they responded only to targeted requests for information.
“We do not provide any government organization with direct access to Facebook servers,” said Joe Sullivan, chief security officer for Facebook.
“We have never heard of PRISM,” said Steve Dowling, a spokesman for Apple.
An internal presentation of 41 briefing slides on PRISM, dated April 2013 and intended for senior analysts in the NSA’s Signals Intelligence Directorate, described the new tool as the most prolific contributor to the President’s Daily Brief, which cited PRISM data in 1,477 items last year. According to the slides and other supporting materials obtained by The Post, “NSA reporting increasingly relies on PRISM” as its leading source of raw material, accounting for nearly 1 in 7 intelligence reports.
The technology companies, whose cooperation is essential to PRISM operations, include most of the dominant global players of Silicon Valley, according to the document. They are listed on a roster that bears their logos in order of entry into the program: “Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.”
“As it is written, there is nothing to prohibit the intelligence community from searching through a pile of communications, which may have been incidentally or accidentally been collected without a warrant, to deliberately search for the phone calls or e-mails of specific Americans,” Udall said.
Even when the system works just as advertised, with no American singled out for targeting, the NSA routinely collects a great deal of American content. That is described as “incidental,” and it is inherent in contact chaining, one of the basic tools of the trade.
In exchange for immunity from lawsuits, companies such as Yahoo and AOL are obliged to accept a “directive” from the attorney general and the director of national intelligence to open their servers to the FBI’s Data Intercept Technology Unit, which handles liaison to U.S. companies from the NSA. In 2008, Congress gave the Justice Department authority for a secret order from the Foreign Surveillance Intelligence Court to compel a reluctant company “to comply.”
There has been “continued exponential growth in tasking to Facebook and Skype,” according to the PRISM slides.
According to a separate “User’s Guide for PRISM Skype Collection,” that service can be monitored for audio when one end of the call is a conventional telephone and for any combination of “audio, video, chat, and file transfers” when Skype users connect by computer alone. Google’s offerings include Gmail, voice and video chat, Google Drive files, photo libraries, and live surveillance of search terms.
Tomi Engdahl says:
Blogger, With Focus on Surveillance, Is at Center of a Debate
http://www.nytimes.com/2013/06/07/business/media/anti-surveillance-activist-is-at-center-of-new-leak.html?pagewanted=all&_r=0
Late Wednesday, Mr. Greenwald, a lawyer and longtime blogger, published an article in the British newspaper The Guardian about the existence of a top-secret court order allowing the National Security Agency to monitor millions of telephone logs.
Tomi Engdahl says:
Mozilla and 85 others send an anti-PRISM letter to Congress
http://www.theinquirer.net/inquirer/news/2274194/mozilla-and-85-others-send-an-antiprism-letter-to-congress
A LARGE ASSORTMENT OF INTERNET and software firms as well as civil liberties groups including the Electronic Frontier Foundation (EFF) have expressed their firm opposition to Orwellian US National Security Agency (NSA) PRISM surveillance of the internet.
Tomi Engdahl says:
Mozilla, ACLU, others join fight against NSA domestic spying
Congress, courts urged to take immediate action
http://www.theregister.co.uk/2013/06/12/mozilla_aclu_vs_nsa/
In response to the recent revelations of massive, secret surveillance programs conducted by the US National Security Agency (NSA), organizations, businesses, and activists across the country are taking action.
On Tuesday, Mozilla announced that it has assembled a broad coalition of almost 100 groups and individuals aimed at pressuring Congress to take action address the issue of domestic spying.
Tomi Engdahl says:
Thanks, NSA: Amazon sales of Orwell’s 1984 rise 9,500%
Citizens of Oceania bone up on the new reality
http://www.theregister.co.uk/2013/06/12/orwell_1984_sales_rocket/
A glance at the “Movers and Shakers” page of Amazon shows there’s been an unusual reaction to the current NSA spying scandal: sales of George Orwell’s classic dystopian novel Nineteen Eighty-Four are up 9,538 per cent.
It was somewhat ironic that the news of the NSA’s systematic slurping of phone records and the subsequent revelations about the PRISM spying system were revealed in the same week as the 64th anniversary of the publication of Orwell’s dark masterpiece. Now it seems people are buying it up either to learn about what could be, or simply because recent events reminded them to read the classic.
Tomi Engdahl says:
Majority Views NSA Phone Tracking as Acceptable Anti-terror Tactic
Public Says Investigate Terrorism, Even If It Intrudes on Privacy
http://www.people-press.org/2013/06/10/majority-views-nsa-phone-tracking-as-acceptable-anti-terror-tactic/
A majority of Americans – 56% – say the National Security Agency’s (NSA) program tracking the telephone records of millions of Americans is an acceptable way for the government to investigate terrorism, though a substantial minority – 41% – say it is unacceptable. And while the public is more evenly divided over the government’s monitoring of email and other online activities to prevent possible terrorism, these views are largely unchanged since 2002, shortly after the 9/11 terrorist attacks.
Young Differ on Principle, but Less on Practice
Younger Americans are more likely than older age groups to prioritize protecting personal privacy over terrorism investigations. Among people ages 18-29, 45% say it is more important 6-10-13 #6for the federal government NOT to intrude on personal privacy, even if that limits its ability to investigate possible terrorist threats. That view falls to 35% among those ages 30-49 and just 27% among those ages 50 and older.
Tomi Engdahl says:
Mobile telephony in the Netherlands has been intercepted since early 2000, and then stored in bulk keywords searched by Dutch intelligence sources claim against De Telegraaf.
When the secret service AIVD around 2006 looking for new ways to use intelligence operations, internet was a fierce debate going on internally or intercepting mobile no better basis for continued making inquiries. “The leadership then called: we must not search the Internet, but all continue to save the massive mobile traffic and therein keywords search,”
Source: http://translate.google.com/translate?sl=nl&tl=en&js=n&prev=_t&hl=en&ie=UTF-8&u=http%3A%2F%2Fwww.telegraaf.nl%2Fbinnenland%2F21642600%2F__Gesprekken_al_jaren_afgetapt__.html
Tomi Engdahl says:
NSA Surveillance May Have Dealt Major Blow To Global Internet Freedom Efforts
http://www.forbes.com/sites/tarunwadhwa/2013/06/13/with-nsa-surveillance-us-government-may-have-dealt-major-blow-to-global-internet-freedom-efforts/
The internet has never been a perfect tool for advancing democracy and human rights.
Despite the most optimistic techno-utopian projections, the internet has yet to set us free and rid the world of dictators. Critics have been right to warn us of the dangers of a single-minded approach
As the internet has grown in usage and importance in our daily lives, so too has the difficulty of keeping it “free” from censorship and control. This struggle was important enough to 29-year-old former Booz Allen employee Edward Snowden for him to give up his life, career, and freedom to leak a historic amount of classified information about the shocking size and depth of the American surveillance state. The fallout is just beginning – and as of now, there are far more questions than answers.
One thing has become clear though: the credibility of the idea that the internet can be a positive, freedom-promoting global force is facing its largest challenge to date. And it comes directly from one of its most outspoken supporters: the US government.
Simply put, the US government has failed in its role as the “caretaker” of the internet. Although this was never an official designation, America controls much of the infrastructure, and many of the most popular services online are provided by a handful of American companies.
Reasonable minds can disagree over the necessity of these programs and how to strike the proper balance between security and privacy.
In the court of global public opinion, America may have tarnished its moral authority to question the surveillance practices of other nations – whether it be Russia on monitoring journalists, or China on conducting cyber espionage.
The costs of surveillance and data storage technologies are plummeting — these will no longer be prohibitive factors. Diplomatic pressures and legal barriers that had also once served as major deterrents will soon fade away. The goal has been to promote internet freedom around the world, but we may have also potentially created a blueprint for how authoritarian governments can store, track, and mine their citizens’ digital lives.
Tomi says:
This information iPhone, Lumia and Android phones transmit the United States
Calls, text messages, location information – a lot of things, including U.S. intelligence agencies can apparently be accessed. Also the Finnish smartphone data is likely to be achieved if desired.
The U.S. intelligence community NSA can get your hands on the most popular smartphone data. About a week ago revealed that, among other things, Microsoft, Google and Apple have given the NSA for information about users of their services.
Leak shows that NSA has a firm grip on smartphones, as Apple, Google and Microsoft share the majority of the smartphone market.
What information you can get from the mobile phone?
1 Who is calling you, and because
Google can store your data on Android phones for calls.
2 Address and credit card number
If you register as Apple, Google or Microsoft’s application store, he must notify his name and address, phone and other contact details and credit card numbers.
3 With your contact information
The companies also offer cloud services, which can back up your phone content.
4 Your text message
Google can save Android users, at least for SMS routing information. Windows Phone 8, Phone users can activate the automatic backup,
Apple again seeks to replace the text in their own iMessage service.
US-based servers.
5 Where you are and move
As well as Google, Apple and Microsoft for example, store a user’s location from the map or the other Services.
6 Your photos
Photos may also include location information, so they can be transmitted with the data, where they were taken.
7 Web browsing and search
The companies will also record the websites you visit to your phone’s browser. Google will also save your searches times. So does Microsoft’s Bing search service.
8 Your speech, your nickname and family tree
Apple iPhone’s Siri voice-hour service for the spoken word will be sent to Apple. At the same time Apple Siri can be stored in the interest of users and nicknames, address book contacts, nicknames, as well as the relations between persons.
Also, Windows Phone, voice recognition
9 Your phone’s model and the unique identifier
10, Almost everything else
If Apple’s iPhone, the user accepts the diagnostics and user data collection
Source: http://www.digitoday.fi/tietoturva/2013/06/15/nama-tiedot-iphone–lumia–ja-android-puhelimet-valittavat-yhdysvaltoihin/20138379/66?rss=6
Tomi Engdahl says:
Facebook’s Wi-Fi Spreads in the Wild
http://www.wired.com/business/2013/06/facebook-wifi-spreads/
The idea of offering people free Wi-Fi in exchange for their physical coordinates began at Facebook as a one-off experiment, a project by two engineers during an all-nighter in May 2012. Since then, Facebook has gradually spread what it now calls “Facebook Wi-Fi” further and further beyond the company’s corporate walls, deploying the system to cafes in Palo Alto and San Francisco and even into a line of routers made by Cisco.
The growth of Facebook’s free internet offering underscores the extent to which the social network is trying to vacuum up more and more information about its members, including their physical movements, and how valuable such data has become in selling advertising.
Intended for use in businesses like cafes, Facebook Wi-Fi asks users to “check in” at the business location using their Facebook account. Once they do, or once they click a small opt-out link, they are granted wireless internet access.
In May, Facebook Wi-Fi graduated beyond experiment as Cisco announced the service would be included as an optional service on its Meraki line of routers.
Tomi Engdahl says:
Mozilla and Stanford Pitch New Cookie Blocking Approach
Laying More Rail for a Do-Not-Track Web
http://adage.com/article/dataworks/mozilla-stanford-pitch-cookie-blocking-approach/242553/
Techno-privacy wonks are laying yet another rail for Do Not Track. Mozilla, maker of the Firefox browser, has paired with the Stanford Center for Internet and Society to create a Cookie Clearinghouse. The project, still in a nascent stage, essentially will be two lists of domains — one that users’ browsers will permit to set cookies and one that will be blocked from doing so.
But the initiative could have a greater impact on digital data privacy than the simple concept suggests.
The effort comes at a time when everyday people are gaining a heightened awareness of rampant data collection by corporations — for logistics and marketing purposes — that in turn fuels National Security Administration surveillance. It also comes at a time of introspection among those involved in the development of a Do Not Track standard at the Worldwide Web Consortium, whose work is now more than a year and a half overdue. Some who have been working on that project, including Stanford privacy activist Jonathan Mayer, believe it may need to draw to a close with no resolution.
A small group of stakeholders including Mozilla, Stanford and browser maker Opera Software will guide the new clearinghouse, which in part is intended to clarify some elements of a patch designed for Mozilla’s Firefox browser that would block third-party cookies by default
Mozilla and Stanford will support opt-out cookies set by the Digital Advertising Alliance, which operates the ad industry’s Ad Choices privacy program, and let users choose to enable tracking by particular sites if they want. “We will support that user choice,” said Ms. McDonald.
Tomi Engdahl says:
Anger mounts after Facebook’s ‘shadow profiles’ leak in bug
http://www.zdnet.com/anger-mounts-after-facebooks-shadow-profiles-leak-in-bug-7000017167/
Summary: Facebook said Friday it fixed a bug that exposed contact info for over six million accounts. The admission revealed its ‘shadow profile’ data collection activities, and users are furious.
Friday Facebook announced the fix of a bug it said inadvertently exposed the private information of over six million users when Facebook’s previously unknown shadow profiles accidentally merged with user accounts in data history record requests.
According to Reuters, the data leak spanned a year beginning in 2012.
Tomi Engdahl says:
Important Message from Facebook’s White Hat Program
https://www.facebook.com/notes/facebook-security/important-message-from-facebooks-white-hat-program/10151437074840766
Joya Kopper says:
I would like to thanks for the efforts you have put in writing this website. I’m hoping the same high-grade weblog post from you in the upcoming as well. In fact your creative writing abilities has inspired me to get my own weblog now. Actually the blogging is spreading its wings rapidly. Your write up is a good example of it.
Tomi says:
Attention, Shoppers: Store Is Tracking Your Cell
http://www.nytimes.com/2013/07/15/business/attention-shopper-stores-are-tracking-your-cell.html?adxnnl=1&pagewanted=all&adxnnlx=1373868399-Q5cZRpR3BHVoBhy37HPvIg
Like dozens of other brick-and-mortar retailers, Nordstrom wanted to learn more about its customers — how many came through the doors, how many were repeat visitors — the kind of information that e-commerce sites like Amazon have in spades. So last fall the company started testing new technology that allowed it to track customers’ movements by following the Wi-Fi signals from their smartphones.
“We did hear some complaints,” said Tara Darrow, a spokeswoman for the store. Nordstrom ended the experiment in May, she said, in part because of the comments.
Nordstrom’s experiment is part of a movement by retailers to gather data about in-store shoppers’ behavior and moods, using video surveillance and signals from their cellphones and apps to learn information as varied as their sex, how many minutes they spend in the candy aisle and how long they look at merchandise before buying it.
But while consumers seem to have no problem with cookies, profiles and other online tools that let e-commerce sites know who they are and how they shop, some bristle at the physical version, at a time when government surveillance — of telephone calls, Internet activity and Postal Service deliveries — is front and center because of the leaks by Edward J. Snowden.
“Way over the line,” one consumer posted to Facebook in response to a local news story about Nordstrom’s efforts at some of its stores.
“The idea that you’re being stalked in a store is, I think, a bit creepy, as opposed to, it’s only a cookie — they don’t really know who I am,”
Cameras have become so sophisticated, with sharper lenses and data-processing, that companies can analyze what shoppers are looking at, and even what their mood is.
For example, Realeyes, based in London, which analyzes facial cues for responses to online ads, monitors shoppers’ so-called happiness levels in stores and their reactions at the register.
Nomi, of New York, uses Wi-Fi to track customers’ behavior in a store, but goes one step further by matching a phone with an individual.
When a shopper has volunteered some personal information, either by downloading a retailer’s app or providing an e-mail address when using in-store Wi-Fi, Nomi pulls up a profile of that customer
If these methods seem intrusive, at least some consumers seem happy to trade privacy for deals.
Sean John Sj4043 says:
Evidently reviewing this topic I like it as it is valid and it is great seeing a writer that’s showing this online to review
Tomi says:
Google’s Data-Trove Dance
Internal Debates Arise Over Using Collected Information and Protecting Privacy
http://online.wsj.com/article_email/SB10001424127887324170004578635812623154242-lMyQjAxMTAzMDMwMDEzNDAyWj.html
In 2011, Google Inc. GOOG +0.98% Chief Executive and co-founder Larry Page asked executives to develop a new, simplified privacy tool that would act as a kind of sliding scale
Because Google has so many Web services that operate differently, executives found it impossible to reduce privacy controls to so few categories, these people said. Also, allowing people to select the maximum-protection setting, known as the “tin-foil-hat option,” went against Google’s newer efforts to get more people to share information about themselves on the Google+ social-networking service, they said.
Technology companies say they care about user privacy and seek to shield their users from unwarranted government intrusion, but they are collecting and sifting increasing volumes of user data from which they profit. For most consumers, providing personal information for Web services is a worthwhile trade. Others object to having their online lives tracked and analyzed.
Thousands of Data ‘Events’
Every hour, an active Google user can generate hundreds or thousands of data “events” that Google stores in its computers, said people familiar with its data-gathering process.
These include when people use Google’s array of Web and mobile-device services, which have long collected information about what individuals are privately searching for on the Web. It includes the videos they watch on YouTube, which gets more than one billion visitors a month; phone calls they’ve made using Google Voice and through nearly one billion Google-powered Android smartphones; and messages they send via Android phones or through Gmail, which has more than 425 million users.
If a user signs in to his or her Google account to use Gmail and other services, the information collected grows and is connected to the name associated with the account. Google can log information about the addresses of websites that person visits after doing Google searches.
Even if the person visits sites without first searching for them on Google, the company can collect many of the website addresses people using Google’s Chrome Web browser or if they visit one of millions of sites that have pieces of Google code, such as its “+1″ button, installed.
Tomi says:
Moscow Subway To Use Special Devices To Read Data On Passengers’ Phones
http://mobile.slashdot.org/story/13/07/30/215231/moscow-subway-to-use-special-devices-to-read-data-on-passengers-phones
“‘The head of police for Moscow’s subway system has said stations will soon be equipped with devices that can read the data on the mobile telephones of passengers. In the July 29 edition of Izvestia, Moscow Metro police chief Andrei Mokhov said the device would be used to help locate stolen mobile phones.”
Tomi says:
XKeyscore: NSA tool collects ‘nearly everything a user does on the internet’
http://www.theguardian.com/world/2013/jul/31/nsa-top-secret-program-online-data
• XKeyscore gives ‘widest-reaching’ collection of online data
• NSA analysts require no prior authorization for searches
• Sweeps up emails, social media activity and browsing history
• NSA’s XKeyscore program – read one of the presentations
A top secret National Security Agency program allows analysts to search with no prior authorization through vast databases containing emails, online chats and the browsing histories of millions of individuals, according to documents provided by whistleblower Edward Snowden.
The NSA boasts in training materials that the program, called XKeyscore, is its “widest-reaching” system for developing intelligence from the internet.
The latest revelations will add to the intense public and congressional debate around the extent of NSA surveillance programs.
XKeyscore, the documents boast, is the NSA’s “widest reaching” system developing intelligence from computer networks – what the agency calls Digital Network Intelligence (DNI). One presentation claims the program covers “nearly everything a typical user does on the internet”, including the content of emails, websites visited and searches, as well as their metadata.
Analysts can also use XKeyscore and other NSA systems to obtain ongoing “real-time” interception of an individual’s internet activity.
Under US law, the NSA is required to obtain an individualized Fisa warrant only if the target of their surveillance is a ‘US person’, though no such warrant is required for intercepting the communications of Americans with foreign targets.
In a second Guardian interview in June, Snowden elaborated on his statement about being able to read any individual’s email if he had their email address. He said the claim was based in part on the email search capabilities of XKeyscore, which Snowden says he was authorized to use while working as a Booz Allen contractor for the NSA.
Beyond emails, the XKeyscore system allows analysts to monitor a virtually unlimited array of other internet activities, including those within social media.
The XKeyscore program also allows an analyst to learn the IP addresses of every person who visits any website the analyst specifies.
this link says:
Wow, marvelous blog layout! How long have you ever been blogging for? you make blogging glance easy. The full glance of your web site is great, as smartly as the content material!
Tomi Engdahl says:
What the NSA can do with “big data”
The NSA can’t capture everything that crosses the Internet—but doesn’t need to.
http://arstechnica.com/information-technology/2013/06/what-the-nsa-can-do-with-big-data/
One organization’s data centers hold the contents of much of the visible Internet—and much of it that isn’t visible just by clicking your way around. It has satellite imagery of much of the world and ground-level photography of homes and businesses and government installations tied into a geospatial database that is cross-indexed to petabytes of information about individuals and organizations. And its analytics systems process the Web search requests, e-mail messages, and other electronic activities of hundreds of millions of people.
No one at this organization actually “knows” everything about what individuals are doing on the Web, though there is certainly the potential for abuse. By policy, all of the “knowing” happens in software, while the organization’s analysts generally handle exceptions (like violations of the law) picked from the flotsam of the seas of data that their systems process.
We know some of this thanks to an earlier whistleblower—former AT&T employee Mark Klein, who revealed in 2006 that AT&T had helped NSA install a tap into the fiber backbone for AT&T’s WorldNet, “splitting” the traffic to run into a Narus Insight Semantic Traffic Analyzer. (The gear has since been rebranded as “Intelligence Traffic Analyzer,” or ITA.)
Narus’ gear was also used by the FBI as a replacement for its homegrown “Carnivore” system. It scans packets for “tag pairs”—sets of packet attributes and values that are being monitored for—and then grabs the data for packets that match the criteria.
In an interview I conducted with Narus’ director of product management for cyber analytics Neil Harrington in September of 2012, Harrington said the company’s Insight systems can analyze and sort gigabits of data each second. “Typically with a 10 gigabit Ethernet interface, we would see a throughput rate of up to 12 gigabits per second with everything turned on. So out of the possible 20 gigabits, we see about 12. If we turn off tag pairs that we’re not interested in, we can make it more efficient.”
A single Narus ITA is capable of processing the full contents of 1.5 gigabytes worth of packet data per second. That’s 5400 gigabytes per hour, or 129.6 terabytes per day, for each 10-gigabit network tap. All that data gets shoveled off to a set of logic servers using a proprietary messaging protocol, which process and reassemble the contents of the packets, turning petabytes per day into gigabytes of tabular data about traffic—the metadata of the packets passing through the box— and captured application data.
NSA operates many of these network tap operations both in the US and around the world.
Storing it, indexing it, and analyzing it in volume required technology beyond what was generally available commercially. Considering that, according to Cisco, the total world Internet traffic for 2012 was 1.1 exabytes per day is physically impossible, let alone practical, for the NSA to capture and retain even a fraction of the world’s Internet traffic on a daily basis.
There’s also the issue of intercepting packets protected by Secure Socket Layer (SSL) encryption. Breaking encryption of SSL-protected traffic is, under the best of circumstances, computationally costly and can’t be applied across the whole of Internet traffic (despite the apparent certificate-cracking success demonstrated by the Flame malware attack on Iran). So while the NSA can probably do it, they probably can’t do it in real-time.
NSA is still collecting call data records for all domestic calls and calls between US and foreign numbers
“comprehensive communications routing information, including but not limited to session identifying information (e.g., originating and terminating telephone number, International Mobile Subscriber Identity (IMEI) number, etc.), trunk identifier, telephone calling card numbers, and time and duration of call.”
In 2006, USA Today called the call database “the largest database in the world.”
BigTable and Hadoop-based databases offered a way to handle huge amounts of data being captured by the NSA’s operations, but they lacked something critical to intelligence operations: compartmentalized security (or any security at all, for that matter). So in 2008, NSA set out to create a better version of BigTable, called Accumulo—now an Apache Foundation project.
Accumulo is a “NoSQL” database, based on key-value pairs. It’s a design similar to Google’s BigTable or Amazon’s DynamoDB, but Accumulo has special security features designed for the NSA, like multiple levels of security access. The program is built on the open-source Hadoop platform and other Apache products.
One of those is called Column Visibility—a capability that allows individual items within a row of data to have different classifications.
Accumulo also can generate near real-time reports from specific patterns in data. So, for instance, the system could look for specific words or addressees in e-mail messages that come from a range of IP addresses; or, it could look for phone numbers that are two degrees of separation from a target’s phone number. Then it can spit those chosen e-mails or phone numbers into another database, where NSA workers could peruse it at their leisure.
In other words, Accumulo allows the NSA to do what Google does with your e-mails and Web searches—only with everything that flows across the Internet, or with every phone call you make.
One of the obstacles to NSA monitoring of Internet communications is SSL. On the surface, “cloud” services such as Gmail, Facebook, and the service formerly known as Hotmail have made that problem harder to overcome as they’ve pulled more interactions in behind SSL-protected sessions. But ironically, those communications services actually started to make it easier for the NSA to collect that protected data through the PRISM program.
PRISM gives the NSA an online connection to cloud providers.
The NSA could theoretically export much of the metadata from these services—without having a specific target—in order to preserve data in the event that the NSA has cause to perform a search. But it’s unlikely, simply for storage capacity reasons, that they copy the application data itself—e-mails, attachments, etc.—on a large scale.
The NSA could theoretically export much of the metadata from these services—without having a specific target—in order to preserve data in the event that the NSA has cause to perform a search. But it’s unlikely, simply for storage capacity reasons, that they copy the application data itself—e-mails, attachments, etc.—on a large scale.
Tomi Engdahl says:
NSA “touches” more of Internet than Google
In deep packet inspection, it’s not the size of the data that matters.
http://arstechnica.com/information-technology/2013/08/the-1-6-percent-of-the-internet-that-nsa-touches-is-bigger-than-it-seems/
According to figures published by a major tech provider, the Internet carries 1,826 Petabytes of information per day. In its foreign intelligence mission, NSA touches about 1.6 percent of that. However, of the 1.6 percent of the data, only 0.025 percent is actually selected for review. The net effect is that NSA analysts look at 0.00004 percent of the world’s traffic in conducting their mission—that’s less than one part in a million.
Put another way, if a standard basketball court represented the global communications environment, NSA’s total collection would be represented by an area smaller than a dime on that basketball court.
The numbers are no real surprise—we’ve already discussed how the laws of physics would make it impossible for the NSA to capture everything, or even a significant portion of everything, that passes over the Internet. But they’re also misleading. In the world of deep packet inspection, verbs like “touch,” “select,” “collect,” and “look at” don’t begin to adequately describe what is going on or what information is extracted from traffic in the process. Considering all that’s within what flows across the Internet, 1.6 percent could hold a significant portion of the metadata describing person-to-person communications.
While 29.21 petabytes is a fraction of the overall traffic on the Internet, it is the equivalent of the traffic that passes through several major Internet exchanges each day. It amounts roughly to 2.77 terabits per second—more than the average throughput of the Equinix exchange network, the CoreSite Any2 Exchange, New York International Internet Exchange (NYIIX), and Seattle Internet Exchange (SIX) combined. In other words, the 1.6 percent of the total of Internet traffic “touched” by the NSA could easily contain much of the traffic passing through the US’ core networks. It can certainly include all the traffic inbound from and outbound to other nations.
The NSA has approximately 150 XKeyscore collection points worldwide. To reach 29.21 petabytes per day, XKeyscore sites pull in around 190 terabytes a day. And to keep the three-day “buffer” XKeyscore holds of captured traffic, that would mean the sites have an average of about 600 terabytes of storage—the equivalent of a fairly manageable 150 4-TB drives.
Regardless how much data flows through the NSA’s tap points, all of it is getting checked. While the NSA may “touch” only 29.21 petabytes of data a day, it runs its digital fingers through everything that flows through the tap points to do so.
The NSA’s XKeyscore uses packet analyzers, the hardware plugged into the network that diverted Internet data is routed down, to look at the contents of network traffic as it passes by. The packet analyzers use a set of rules to check each packet they “see” as it is read by the analyzers’ software into memory.
Packets that don’t meet any of the rules that have been configured are sent along unmolested.
Packets that match one or more of the rules get routed to processing servers for further analysis. Those rules can be very broad—”grab everything with an IP address in its header that is outside the United States,” for example—or they can look for very specific patterns within packets, such as those of VPN and website log-ins, Skype and VoIP traffic, or e-mails with attachments.
Tomi Engdahl says:
Amid Data Controversy, NSA Builds Its Biggest Data Farm
http://www.npr.org/2013/06/10/190160772/amid-data-controversy-nsa-builds-its-biggest-data-farm
As privacy advocates and security experts debate the validity of the National Security Agency’s massive data gathering operations, the agency is putting the finishing touches on its biggest data farm yet.
The gargantuan $1.2 billion complex at a National Guard base 26 miles south of Salt Lake City features 1.5 million square feet of top secret space. High-performance NSA computers alone will fill up 100,000 square feet.
The Utah Data Center is a data farm that will begin harvesting emails, phone records, text messages and other electronic data in September.
Tomi Engdahl says:
Google Tells Court You Cannot Expect Privacy When Sending Messages to Gmail — People Who Care About Privacy Should Not Use Service, Consumer Watchdog Says
http://www.consumerwatchdog.org/newsrelease/google-tells-court-you-cannot-expect-privacy-when-sending-messages-gmail-people-who-care
Google’s brief said: “Just as a sender of a letter to a business colleague cannot be surprised that the recipient’s assistant opens the letter, people who use web-based email today cannot be surprised if their emails are processed by the recipient’s [email provider] in the course of delivery. Indeed, ‘a person has no legitimate expectation of privacy in information he voluntarily turns over to third parties.’” (Motion to dismiss, Page 19)
Consumer Watchdog said today that people who care about their email correspondents’ privacy should not use the Internet giant’s service.
Tomi Engdahl says:
Google: Cloud users have ‘no legitimate expectation of privacy’
Third-party handling means just that, says court filing
http://www.theregister.co.uk/2013/08/14/google_cloud_users_have_no_legitimate_expectation_of_privacy/
“Just as a sender of a letter to a business colleague cannot be surprised that the recipient’s assistant opens the letter, people who use web-based email today cannot be surprised if their emails are processed by the recipient’s [email provider] in the course of delivery,” the motion reads.
“Indeed, ‘a person has no legitimate expectation of privacy in information he voluntarily turns over to third parties.’”
When you read through the full filing, however, it turns out that Google’s assertion is legally correct. In 1979, the US Supreme Court considered the case of Smith v. Maryland, appealing the use of a wiretap on a telephone, and they ruled that:
Since the defendant had disclosed the dialed numbers to the telephone company so they could connect his call, he did not have a reasonable expectation of privacy in the numbers he dialed.
Google is making the same argument when it comes to keyword searching for advertising, and the law is on its side; the Electronic Communications Privacy Act allows such indexing. It’s doubly covered because indexing is included in Gmail’s terms and conditions.
“Google has finally admitted they don’t respect privacy,” said John Simpson, privacy project director of Consumer Watchdog, the non-profit that publicized the court motion. “People should take them at their word; if you care about your email correspondents’ privacy don’t use Gmail.”
Tomi Engdahl says:
Teens really realize what social media can reveal
Contrary to popular belief, teens care about their privacy online. The Pew Research Center study 12 to 17-year-olds perceptions of online privacy.
The study also revealed that 70 percent of teens have asked for advice to manage their privacy. Many adults may be surprised that the parents and the guys are just as important advisors.
42% asked for advice from friends online privacy manage
41% of parents
37% said his sister or serkultaa
13% sought information on the website
9% said the teacher
3% asked from some outside
12 to 13 per cent of girls aged 77 has asked for privacy management advice, the boys, the figure is 66 per cent.
“Privacy Settings are easy., I think that they [Facebook] modify them often, reset or something. So they have to constantly update themselves,” said one of the study participated in the 13-year-old son.
Source: http://www.tietoviikko.fi/kaikki_uutiset/teinit+kylla+tajuavat+mita+somessa+voi+paljastaa/a922250
Tomi Engdahl says:
New Details Show Broader NSA Surveillance Reach
Programs Cover 75% of Nation’s Traffic, Can Snare Emails
http://online.wsj.com/article_email/SB10001424127887324108204579022874091732470-lMyQjAxMTAzMDIwMDEyNDAyWj.html
The National Security Agency—which possesses only limited legal authority to spy on U.S. citizens—has built a surveillance network that covers more Americans’ Internet communications than officials have publicly disclosed, current and former officials say.
The system has the capacity to reach roughly 75% of all U.S. Internet traffic in the hunt for foreign intelligence, including a wide array of communications by foreigners and Americans. In some cases, it retains the written content of emails sent between citizens within the U.S. and also filters domestic phone calls made with Internet technology, these people say.
The NSA’s filtering, carried out with telecom companies, is designed to look for communications that either originate or end abroad, or are entirely foreign but happen to be passing through the U.S. But officials say the system’s broad reach makes it more likely that purely domestic communications will be incidentally intercepted and collected in the hunt for foreign ones.
The programs, code-named Blarney, Fairview, Oakstar, Lithium and Stormbrew, among others, filter and gather information at major telecommunications companies.
The NSA defends its practices as legal and respectful of Americans’ privacy.
The NSA’s U.S. programs have been described in narrower terms in the documents released by former NSA contractor Edward Snowden. One, for instance, acquires Americans’ phone records; another, called Prism, makes requests for stored data to Internet companies. By contrast, this set of programs shows the NSA has the capability to track almost anything that happens online, so long as it is covered by a broad court order.
Tomi Engdahl says:
This Software Won’t Let You Look Away
The creepiest educational technology yet
http://www.theatlantic.com/technology/archive/2013/08/this-software-wont-let-you-look-away/278812/
It’s hard to imagine a creepier educational technology than “FocusAssist,” a new feature announced by online training company Mindflash last week. Designed to be used in corporate training courses on iPad, FocusAssist, according to Businessweek:
uses the tablet’s camera to track a user’s eye movements. When it senses that you’ve been looking away for more than a few seconds (because you were sending e-mails, or just fell asleep), it pauses the course, forcing you to pay attention–or at least look like you are–in order to complete it.
Yeesh. FocusAssist forces users to pay attention to Mindflash’s videos.
I was immediately creeped out by this. FocusAssist forces people to perform a very specific action with their eyeballs, on behalf of “remote organizations,” so that they may learn what the organization wants them to learn. Forcing a human’s attention through algorithmic surveillance: It’s the stuff of A Clockwork Orange.
But maybe everything just sounds creepier when you talk about it in corporatese. Is FocusAssist as insidious as it sounds?
Tomi Engdahl says:
Declassified Documents Prove NSA Is Tapping the Internet
http://www.wired.com/threatlevel/2013/08/nsa-tapping-internet/
U.S. intelligence officials have declassified a secret court opinion that both chastises the National Security Agency for misleading the court and highlights an eavesdropping program in which authorities have direct access to “upstream” internet communications.
The document (.pdf) released today confirms for the first time unofficial leaks and speculation that the federal intelligence community has direct access to telecom companies’ backbones and it scoops up email communications as they go past. Millions are collected each year.
WIRED first reported on such an eavesdropping installation in 2007 when a former AT&T technician provided documents outlining eavesdropping technology used by AT&T.
Today’s revelation follows disclosures by NSA leaker Edward Snowden, who highlighted other NSA-backed spy programs, including one called PRISM and another that collects metadata from every phone call made in America.
Tomi Engdahl says:
Be careful, your information falling into the wrong hands
The network commercial services have entered your personal information is not safe. They will end up sooner or later into the wrong hands – the criminals, the authorities, or other businesses. It warns Jyrki Kasvi from Tieke.
Corporate data collected by us online will end up sooner or later into the wrong hands, criminals or authorities. This can happen even if the companies do not use the information unethically. Committee warns of Information Society Development in Tieken of Research and Development, Jyrki Kasvi.
He is concerned about the huge mass of information, which is the private collection of people online.
“We should not simply assume that the information is only in the forums to which you are assigned. Intrusion through which they may end up being criminals, acquisitions, or a secret to another company under the laws of the authorities for analysis. ”
Our knowledge, are the building blocks of Google and Facebook’s online giants such as the actual product, targeted advertising and market analysis, building.
Willingly disclose information about who we spend time with, what we are interested in, where we are moving, where to dream about what we buy, and so on.
About what companies are doing to collect knowledge, is not well understood. Even the revelations of the U.S. NSA spying by the Office of massive data collection of ordinary people in network traffic has received a majority cautious.
Google’s lawyers are even directly stated that people can not expect emails to be private.
The huge masses of information management is no longer a problem, and they can be mined out of the desired things. Servers gigantic industrial buildings keep wheels turning.
“We are living in the open windows on the world. Good times have been going on for so long that people do not know how to be concerned about data misuse. Finnish lacks a healthy paranoia to protect your identity”
Lawyer, to defend the rights of citizens’ electronic Effi Vice-President of Ville Oksanen, estimates that companies are interested in the masses, not individuals.
“I think we should not worry about too much. In normal everyday life of an individual consumer, a relatively small risk that his or her information would be used widely abused. Services using the current price is that it will have to give up some degree of privacy. ”
Facebook knows who your friends are, what you liked, what words to use with your discussions with and which pages you visited when you sign in online.
Google’s services will still have a bias towards a more complete picture. What Google does not know about us? If you make it web search, whereas YouTube videos and use your Android phone, Gmail, Google plus, as well as the Google Wallet payment service, the mysteries are few and far between. Chrome saved passwords are easy to read.
If the smartphone allows the use of location data, location may be, for example, unmask the micro-blogging service Twitter.
“The consent to use location data to provide easily without any further reflection. People often automatically click on “yes” to all questions, “Oksanen says.
Map of services to facilitate the use of spatial data using must be enabled. This increases the incentive for the location of the distribution.
The result will tell you what this can be sold to the consumer.
“To our knowledge allows advertisers to be able to provide those services that are not previously been unimaginable. It is the right advertiser’s holy grail, ” Kasvi will update.
Recruitment situations in the United States also looks at social media. Finnish Personal Data Act prohibits profiling the conclusion of a potential employee online behavior.
The collection of data is not necessarily according to Oksanen’s a bad thing. The problem consists in his opinion, if the data is not able to control.
“A system in which all the information is collected and everything is utilized to change the structures of society. The consumer does not own behavior hardly able to influence the case. Instead, people should be required to policy makers on the protection of the privacy laws. ”
The European Parliament and the European Council have started treatment with EU data protection law reform. The new Data Protection Regulation enters into force, it replaces the Finnish Personal Data Act.
Source: http://www.3t.fi/artikkeli/uutiset/teknologia/varo_tietosi_joutuvat_vaariin_kasiin
Tomi Engdahl says:
Be careful, your information falling into the wrong hands
http://www.3t.fi/artikkeli/uutiset/teknologia/varo_tietosi_joutuvat_vaariin_kasiin
Thus you will be monitored
♦ If you are logged in while surfing one of the service (eg Facebook, Google), you ended up talking about to the service operator, which pages you visit. Also verkkohakusi saved, if you like, for example Gmail open in the background.
♦ Photos reveal. There you can see the shared network, where it was taken, if the location data is not cleared. Do you want to announce such as your home coordinates?
♦ If there is something you do not want anyone outside to know, tell it to your loved ones face to face.
♦ Remember that even though you do not now have other interesting person, 20 years from now you might have. Behave according to the network.
♦ feels hot, all the things you have given of yourself on Facebook? Download the file size of your Facebook history, and your check. Archive for downloading access account settings.
Tomi Engdahl says:
Facebook considers adding profile photos to facial recognition
http://www.reuters.com/article/2013/08/29/us-facebook-facial-idUSBRE97S0UZ20130829
Facebook Inc is considering incorporating most of its 1 billion-plus members’ profile photos into its growing facial recognition database, expanding the scope of the social network’s controversial technology.
Tomi Engdahl says:
Thoughts on privacy
http://blogs.law.harvard.edu/doc/2013/08/31/thoughts-on-privacy/
In Here Is New York, E.B. White opens with this sentence: “On any person who desires such queer prizes, New York will bestow the gift of loneliness and the gift of privacy.” Sixty-four years have passed since White wrote that, and it still makes perfect sense to me, hunched behind a desk in a back room of a Manhattan apartment.
That’s because privacy is mostly a settled issue in the physical world, and a grace of civilized life. Clothing, for example, is a privacy technology. So are walls, doors, windows and shades.
Private spaces in public settings are well understood in every healthy and mature culture.
Worse, the institution we look toward for protection from this kind of unwelcome surveillance — our government — spies on us too, and relies on private companies for help with activities that would be a crime if the Fourth Amendment still meant what it says.
I see two reasons why privacy is now under extreme threat in the digital world — and the physical one too, as surveillance cameras bloom like flowers in public spaces, and as marketers and spooks together look toward the “Internet of Things” for ways to harvest an infinitude of personal data.
The end-to-end principle was back-burnered when client-server (aka calf-cow) got baked into e-commerce in the late ’90s. In a single slide Phil Windley summarizes what happened after that. It looks like this:
The History of E-commerce
1995: Invention of the cookie.
The end.
Another irony: the overlords are nerds too. And they lord over what Bruce Schneier calls a feudal system:
Reason #2
We have loosed three things into the digital world that we (by which I mean everybody) do not yet fully comprehend, much less deal with (through policy, tech or whatever). Those are:
Ubiquitous computing power. In the old days only the big guys had it. Now we all do.
Ubiquitous Internet access. This puts us all at zero virtual distance from each other, at costs that also veer toward zero as well.
Unlimited ability to observe, copy and store data, which is the blood and flesh of the entire networked world.
In tech, what can be done will be done, sooner or later, especially if it’s possible to do it in secret — and if it helps make money, fight a war or both. This is why we have bad acting on a massive scale: from click farms gaming the digital advertising business, to the NSA doing what now know it does.
Tomi Engdahl says:
Marketers may think they know all about me, but they don’t
http://www.citeworld.com/security/22366/acxiom-aboutthedata-wrong
Data broker Acxiom did something a little unusual this week. It launched a service that lets you see the data they’ve collected on you. I decided to test this service by checking out my own data, and what I found surprised me.
The database is similar to many others used by so-called data brokers. These companies gather information on individuals and groups and sell it to advertisers. It’s supposed to give the advertisers an edge in serving ads that are most relevant to any particular person.
Where The Data Comes From
Where do they get this information? Well, according to the Acxiom Aboutthedata.com web site, it comes from public records, surveys and questionnaires we might have filled out, and other undefined collection points. Lessons to be learned from that little bit of information: Be careful what you share about yourself because someone is always collecting it.
Yet given all that information from a variety of sources, I found multiple inaccuracies — some minor, some that were just plain wrong. When you consider all of the information we share on websites on a daily basis, this company’s picture of me was still woefully inadequate.
And I’m pleased about that.
To get started I went to he Aboutthedata.com web site. I had to supply a bunch of information to get started, which made me pause. Was this a scam to get more data about me?
So what did my data look like? Without getting into too much detail because I would rather leave my personal information private, they were not really close on my income
It got the number of kids I have wrong, which is somehow strangely comforting.
They got the easy details about my house right — heck, that’s on Zillow — but they didn’t get any of my mortgage information correct. They had no vehicle data whatsoever, which seems odd
The Economic data got my credit cards right, although not the types
The Shopping section was hard to prove or disprove.
Household Interests got my religious affiliation wrong. But perhaps what I found most amusing was that it indicated my OS of choice was Windows. I haven’t owned a Windows computer in a long time.
The company argues on the website that you’re better off providing advertisers with good information so they can target ads that matter to you instead of garbage, but I will opt out — even if the skeptical side of me believes it doesn’t matter — because correcting the database will only fix the database for them. Why should I do that?
Tomi Engdahl says:
Privacy Scandal: NSA Can Spy on Smart Phone Data
http://www.spiegel.de/international/world/privacy-scandal-nsa-can-spy-on-smart-phone-data-a-920971.html
SPIEGEL has learned from internal NSA documents that the US intelligence agency has the capability of tapping user data from the iPhone, devices using Android as well as BlackBerry, a system previously believed to be highly secure.
The documents state that it is possible for the NSA to tap most sensitive data held on these smart phones, including contact lists, SMS traffic, notes and location information about where a user has been.
The documents also indicate that the NSA has set up specific working groups to deal with each operating system, with the goal of gaining secret access to the data held on the phones.
In the internal documents, experts boast about successful access to iPhone data in instances where the NSA is able to infiltrate the computer a person uses to sync their iPhone. Mini-programs, so-called “scripts,” then enable additional access to at least 38 iPhone features.
The documents suggest the intelligence specialists have also had similar success in hacking into BlackBerrys.
The documents also state that the NSA has succeeded in accessing the BlackBerry mail system, which is known to be very secure. This could mark a huge setback for the company, which has always claimed that its mail system is uncrackable.
Tomi Engdahl says:
India govt reportedly monitors Web activities, without ISP knowledge
http://www.zdnet.com/in/india-govt-reportedly-monitors-web-activities-without-isp-knowledge-7000020396/
Summary: Indian government said to have deployed Lawful Intercept and Monitoring systems to track Internet activities of citizens, separate from similar systems used by telcos in the government’s Central Monitoring System project.
The Indian government is reportedly carrying out Internet surveillance on its citizens, in contrast with the government’s rules and notifications for ensuring communications privacy.
Tomi Engdahl says:
Is Twitter revealing your location without your permission?
http://www.electronicproducts.com/Computer_Peripherals/Communication_Peripherals/Is_Twitter_revealing_your_location_without_your_permission.aspx
Social media has become a part of everyday life. If you have a Facebook or Twitter account, you’re probably even familiar with posts that show a friend’s exact location.
As you may suspect, this can be very dangerous since it allows others to know exactly where you are at all times. So you can opt to turn off your geotagging settings, but what happens when your social media sites can access your location, even if you don’t offer it up.
To deal with this issue, a University of Southern California (USC) researcher has created an application that lets you test your own location footprint.
In his one week sampling period, he found that about 20% of the tweets actually showed a user’s location so accurately that you could locate their exact street or even better.
A lot of users gave their location willingly by using their GPS function.
“The downside is that mining this kind of information can also provide opportunities for criminal misuse of data,” said Weidemann.
Tomi Engdahl says:
‘Do not track’ effort in trouble
http://thehill.com/blogs/hillicon-valley/technology/322701-do-not-track-group-should-give-up-departing-online-ad-reps-say
A key stakeholder is pulling out of talks to create a “do not track” list similar to the popular do not call lists that prevent telemarketers from calling people at home.
The decision by the Digital Advertising Alliance (DAA) to leave the talks is likely to lead to legislation that would impose a do not track list on Internet companies to prevent them from tacking every click by consumers online.
“My own view is that the Working Group does not have a path to consensus that includes large blocs of stakeholders with views as divergent as the DAA, on the one hand, and those seeking stricter privacy rules, on the other,” he said in an email. “I no longer see any workable path to a standard that will gain active support from both wings of the Working Group.”
“If the DAA power brokers — Google, Yahoo, and the ad giants — had really wanted to deliver new privacy protection clout to consumers, our work would have successfully finished a year ago,” Chester said.
But even with the DAA gone, he said the group is unlikely to succeed in creating a “Do Not Tack” standard.
Tomi Engdahl says:
Google may ditch ‘cookies’ as online ad tracker
http://www.usatoday.com/story/tech/2013/09/17/google-cookies-advertising/2823183/
Google is developing an anonymous identifier for advertising, or AdID, that would replace third-party cookies as the way advertisers track people’s Internet browsing activity for marketing purposes.
Google, the world’s largest Internet search company, is considering a major change in how online browsing activity is tracked, a move that could shake up the $120 billion digital advertising industry.
Google, which accounts for about a third of worldwide online ad revenue, is developing an anonymous identifier for advertising, or AdID, that would replace third-party cookies as the way advertisers track people’s Internet browsing activity for marketing purposes, according to a person familiar with the plan.
The AdID would be transmitted to advertisers and ad networks that have agreed to basic guidelines, giving consumers more privacy and control over how they browse the Web, the person said, on condition of anonymity.
Google’s move will be closely watched by the ad industry because the company is not only the leader in online advertising, its Chrome browser is now the world’s most popular, having surged ahead of Microsoft’s Internet Explorer, Mozilla’s Firefox and Apple’s Safari in recent years.
Apple’s Safari browser has blocked third-party cookies since its introduction in 2003, and the technology giant introduced its own ad identifiers for its iOS mobile platform last year.
If Google follows through with its own version of this approach, that could give users more control over how they are tracked online. However, it will also put more power in the hands of two of the largest technology companies, according to some people in the advertising industry.
“There could be concern in the industry about a system that shifts more of the benefits and control to operators like Google or Apple,” said Clark Fredricksen of eMarketer, which tracks the digital ad industry.
The AdID may be automatically reset by the browser every year, and users will be able to create a secondary AdID for online browsing sessions they want to keep particularly private, the person explained.