A New Wireless Hack Can Unlock 100 Million Volkswagens
https://www.wired.com/2016/08/oh-good-new-hack-can-unlock-100-million-volkswagens/
In 2013, when University of Birmingham computer scientist Flavio Garcia and a team of researchers were preparing to reveal a vulnerability that allowed them to start the ignition of millions of Volkswagen cars without keys but were hit with lawsuit to delay publication. Now, a year after that hack was finally publicized, the same researchers show in Usenix security conference how the keyless entry system that unlocks the vehicle’s doors can be hacked with cheap hardware (Arduino and RF module).
The affect the keyless entry systems of an estimated nearly 100 million cars. It applies to almost every Volkswagen cars sold after 1995, and also Audi and Škoda. According to article also some car models from Alfa Romeo, Citroen, Fiat, Ford, Mitsubishi, Nissan, Opel, and Peugeot are affected by this.
There are two different attacks. Researchers find cryptographic keys shared by millions of Volkswagen vehicles can allow them clone key fobs using cheap radio hardware. There are 100 Million Vehicles and only 4 Secret Keys. Attack can be performed remotely using Arduino board with an attached radio receiver that can be purchased for $40.
Semiconductor company NXP been for years recommending customers upgrade to newer schemes from the vulnerable HiTag2 crypto system.
Wireless Hack Threatens Locking System on Nearly All VW Cars Sold Since 1995
http://www.bleepingcomputer.com/news/security/wireless-hack-threatens-locking-system-on-nearly-all-vw-cars-sold-since-1995/
Purchased a car from Volkswagen in the last 20 years? If you did, chances are a group of researchers can now unlock your vehicle using a new wireless hack.
At the 25th Usenix Security Symposium in Austin, Texas, researchers Flavio D. Garcia and David Oswald along with colleagues from the University of Birmingham and the German engineering firm Kasper & Oswald will deliver a presentation entitled, Lock It and Still Lose It —on the (In)Security of Automotive Remote Keyless Entry Systems.
In it, they’ll unveil two security vulnerabilities that together threaten the security of 100 million vehicles made by Volkswagen, Ford, and other well known car manufacturers.
A single cryptographic key that is shared among nearly all vehicles made by the German car manufacturer.
An attacker can essentially clone the key fob to unlock the vehicle. Attackers can allegedly use a radio setup to intercept eight codes sent from a key fob to a target vehicle. Using those codes, the actors can get to work breaking the scheme. An attacker has to be within 300 feet of the car.
This is not the first time researchers have demonstrated automobile-related vulnerabilities. In the summer of 2015, three Jeep owners filed a lawsuit against Chrysler. I have mentioned his case on Hackers Remotely Kill a Jeep on the Highway, Hackers Commandeer a Moving Jeep, Jeep Hacking 101 and The FBI Warns That Car Hacking Is a Real Risk postings.


5 Comments
Tomi Engdahl says:
The English University of Birmingham researchers revealed last week, held in Austin USENIX security conference that millions of Volkswagen Group cars can easily go in without a lock being broken
The car does not, of course, must start from a simple radio signal, but the theft of objects inside the car will become very easy.
According to VW the fault is not included in the following car models: Golf, Tiguan, Touran and Passat. For other models VW are working on repairs.
Source: http://etn.fi/index.php?option=com_content&view=article&id=4838:radiotekniikalla-sisaan-kaikkiin-volkswageneihin&catid=13&Itemid=101
Tomi Engdahl says:
Millions of Volkswagens Can Be Unlocked By Hackers
http://spectrum.ieee.org/cars-that-think/transportation/safety/millions-of-volkswagens-can-be-unlocked-by-hackers?utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+IeeeSpectrum+%28IEEE+Spectrum%29&utm_content=FaceBook
Millions of Volkswagen cars could in principle be unlocked from a distance by hackers, according to a new report. It’s one more strike against a German company that’s had more than its share of bad news, what with VW’s admitted cheating on diesel-emissions tests.
But there’s plenty of bad news to go around: the report notes that many models from other companies have vulnerabilities of their own. And the problem is worse with older cars, designed before carmakers gave much thought to cybersecurity.
Kasper told the BBC that the researchers informed Volkswagen of the vulnerability in late 2015 and that the company was taking steps to mitigate the problem. But he said there are “at least 10 more, very widespread” vulnerabilities affecting other car brands, which the researchers won’t publish until the manufacturers have had time to do something about them.
The report describes two weaknesses.
Tomi Engdahl says:
Arduino + Software Defined Radio = Millions of Vulnerable Volkswagens
http://hackaday.com/2016/08/18/adruino-software-define-radio-millions-of-vulnerable-volkswagens/
As we’ve mentioned previously, the integrity of your vehicle in an era where even your car can have a data connection could be a dubious bet at best. Speaking to these concerns, a soon-to-be published paper (PDF) out of the University of Birmingham in the UK, states that virtually every Volkswagen sold since 1995 can be hacked and unlocked by cloning the vehicle’s keyfob via an Arduino and software defined radio (SDR).
The process isn’t exactly as simple as putting together $40 of electronics and walking away with a vehicle. The would-be thief must be close in order to detect the fob’s unique key — although they only need to do so once for that vehicle! — as well as reverse-engineer the other half of the code from the vehicle’s internal network. Exploiting HiTag2’s vulnerabilities to unlock the vehicle can be achieved within a minute by a well-prepared thief. [Garcia] and his team note that only the VW Golf 7 has been spared from this exploit.
Tomi Engdahl says:
Rohde & Schwarz Show Test System for Remote Keyless Entry Systems
http://www.eetimes.com/document.asp?doc_id=1330814&
At electronica 2016, Rohde & Schwarz is presenting a universal solution for testing vehicle keys and the associated electronic control units with their various wireless technologies. Thanks to the modular and scalable approach, the test system can be used to test at the printed board and device level in all product phases — from development to product qualification to mass production.
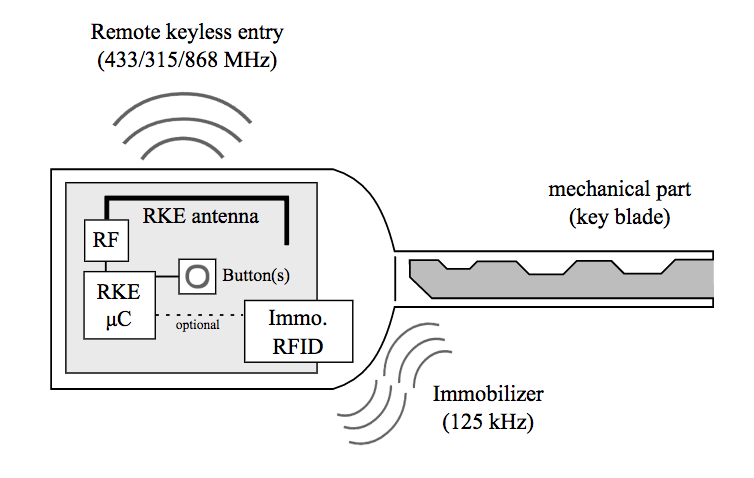
Modern vehicle key systems, such as remote keyless entry (RKE) and passive entry/passive start (PEPS) systems, use a variety of wireless communications standards to transmit encoded signals. In the past, both LF frequencies (e.g. 125 kHz) and UHF frequencies (e.g. 433 MHz) as well as a magnetic compass system that works in three spatial axes (e.g. 21 kHz) were used to locate the key in or near the vehicle.
Using ultra-wideband (UWB) radio, the latest generation of key systems only needs one wireless standard in the non-licensed frequency range between 3.1 and 10.6 GHz. Time of flight (TOF) measurement prevents the relay attacks used to steal vehicles. TOF also makes it possible to determine the location of the key. Some manufacturers use near-field communications (NFC) to use a smartphone as a digital key.
Rohde & Schwarz is showing how a new system solution can help manufacturers meet their testing requirements. The demonstration consists of a fully automatic R&S TS7124AS shielded test box
Tomi Engdahl says:
Unlocking a Subaru with a Raspberry Pi, a 433MHz Radio, and an Unpatched Exploit
The Subaru #fobrob exploit
https://blog.hackster.io/unlocking-a-subaru-with-a-raspberry-pi-a-433mhz-radio-and-an-unpatched-exploit-de0f88dc7c2c