DELTACO USB3-GIGA5 is a USB 3.0 network adapter with internal flash memory, Gigabit, 1xRJ45, 1xUSB3.0 Type A ha, black. It is designed to allow you to connect a network cable to your device that has USB connector but lacks built-in network card with RJ45 jack. The installation is plug and play in Windows 7 and 8, if drivers are needed, they are included on an internal flash memory (The CD-ROM drive appears in the device manager only the first time you connect the adapter to the computer after the adapter is installed correctly, it will no longer be displayed). The interface to computer is SuperSpeed USB 3.0 and connection to network is Gigabit Ethernet (Ethernet 10Base-T, Ethernet 100Base-TX, Ethernet 1000Base-T).
I found this one device that was broken. The USB connector seem to have taken some hit (metal bent). It looked that someone had already tried to open it.
Let’s take a look inside.
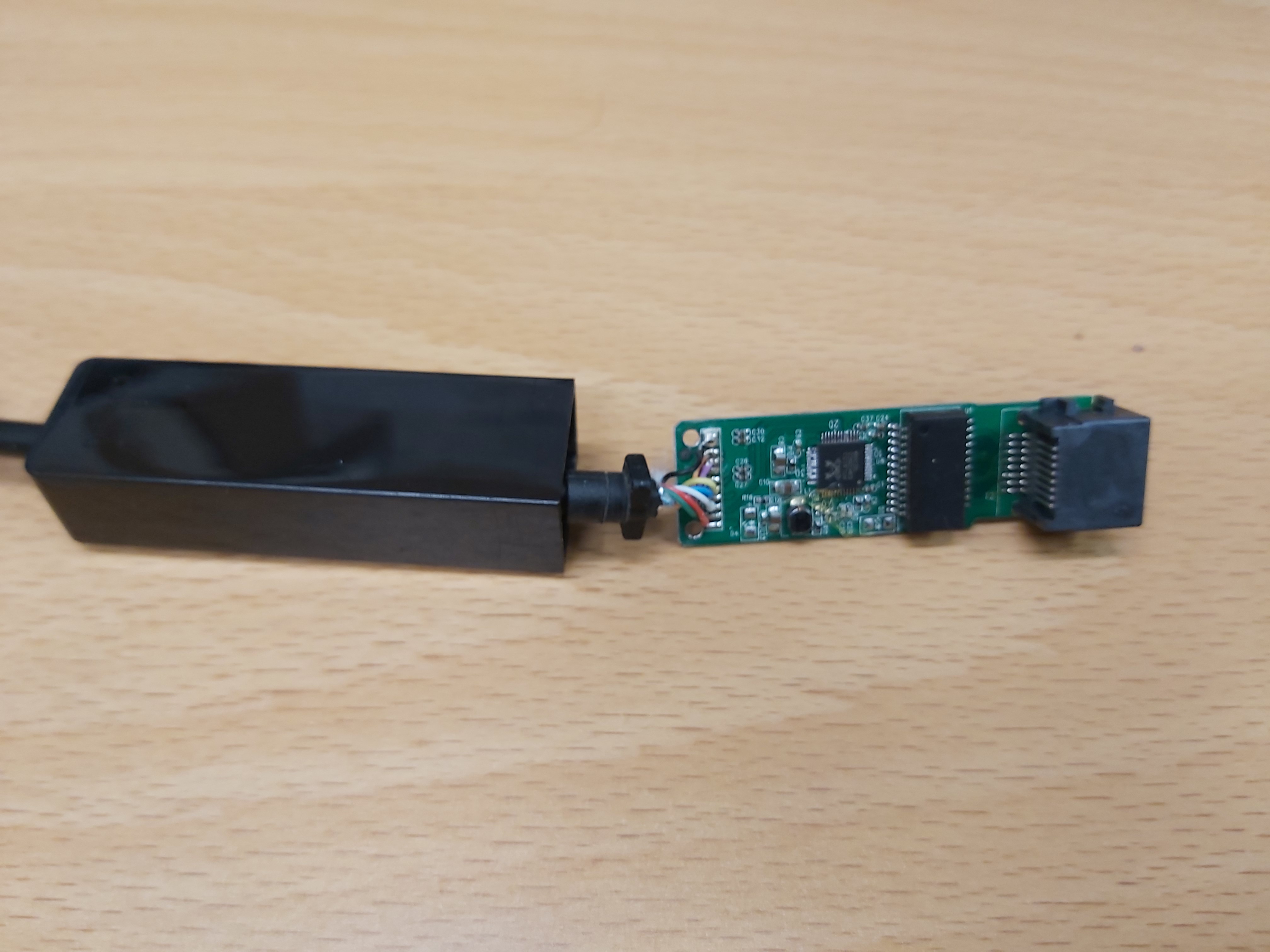
Inside there seems to be a circuit board that starts with USB cable on the left, next there is the main processing chip, Ethernet isolation transformer and RJ-45 connector. That’s pretty much what I expected to see in this kind of device.
Here is close-up view of circuit board.
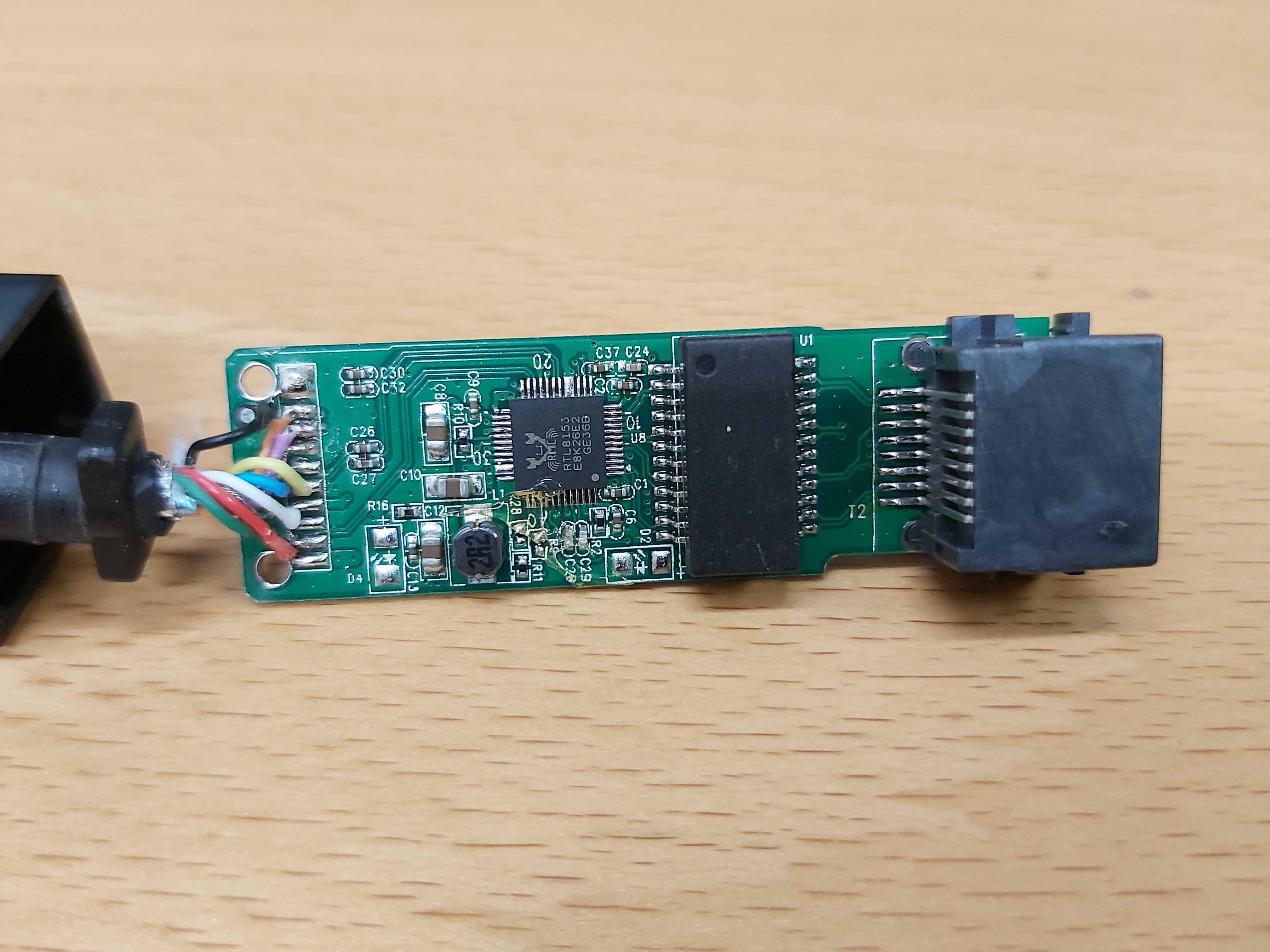
On this side now we can see that the main chip is RTL8153 and Ethernet transformer does not seem to have any marking in it. There is a small ferrite core coil that is most probably for power filtering or to build a small switch more regulator.
https://www.realtek.com/en/products/communications-network-ics/item/rtl8153
RTL8153 is an Integrated 10/100/1000M Ethernet Controller for USB Applications. The Realtek RTL8153-CG 10/100/1000M Ethernet controller combines an IEEE 802.3u compatible Media Access Controller (MAC), USB 3.0 bus controller, and embedded memory. The RTL8153 offers high-speed transmission over CAT 5 UTP cable or CAT 3 UTP (10Mbps only) cable. Functions such as Crossover Detection and Auto-Correction, polarity correction, adaptive equalization, cross-talk cancellation, echo cancellation, timing recovery, and error correction are implemented to provide robust transmission and reception capabilities. The RTL8153 features embedded One-Time-Programmable (OTP) memory that can replace the external EEPROM (93C46/93C56/93C66/TWSI). It supports USB 3.0, 2.0, and 1.1 host interface. The chip has SPI Flash Interface for external memory chip.
The RTL8153 supports Protocol offload: It can offload ARP (IPv4) and NS (IPv6) protocols while in the D3 power saving state. It can do Microsoft NDIS5, NDIS6 Checksum Offload (IPv4, IPv6, TCP, UDP) and Segmentation Task-offload.
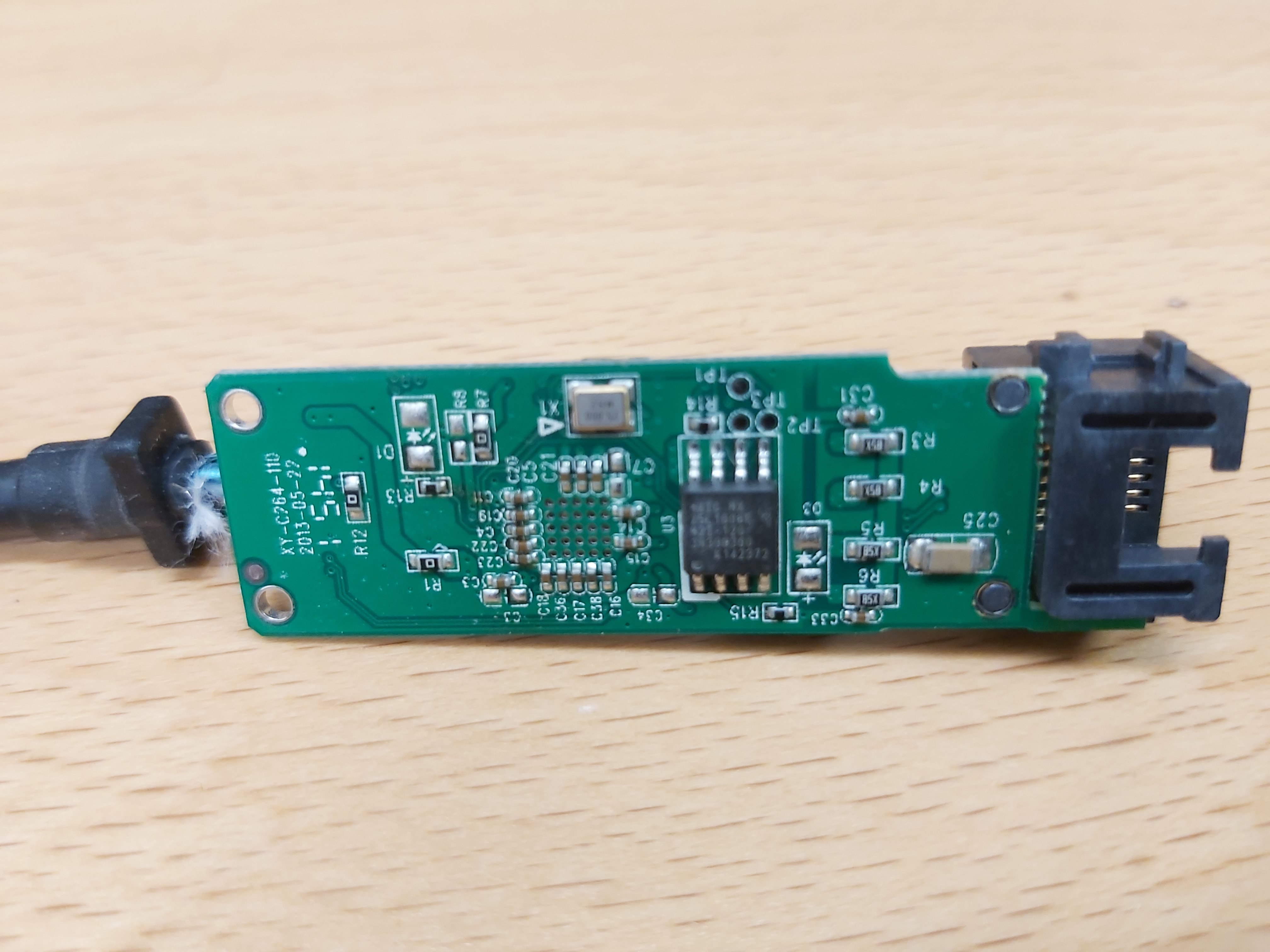
Now let’s take a look at the back side of the circuit board.
Here the notable components are 25 MHz oscillator and MX25L1606E. Macronix MX 25L1606E is a CMOS serial flash memory that uses 2.7 to 3.6 volt for read, erase, and program operations. The device feature a serial peripheral interface and software protocol allowing operation on a simple 3-wire bus. The three bus signals are a clock input (SCLK), a serial data input (SI), and a serial data output (SO). The device supports up to 86MHz serial clock. The memory size is 16M-BIT.



5 Comments
Tomi Engdahl says:
Is Your Device Actually USB 3.0, Or Is The Connector Just Blue?
https://hackaday.com/2022/04/03/is-your-device-actually-usb-3-0-or-is-the-connector-just-blue/
Discount (or even grey market) electronics can be economical ways to get a job done, but one usually pays in other ways. [Majenko] ran into this when a need to capture some HDMI video output ended up with rather less than was expected.
Faced with two similar choices of discount HDMI capture device, [Majenko] opted for the fancier-looking USB 3.0 version over the cheaper USB 2.0 version, reasoning that the higher bandwidth available to a USB 3.0 version would avoiding the kind of compression necessary to shove high resolution HDMI video over a more limited USB 2.0 connection.
https://majenko.co.uk/blog/our-blog-1/usb-3-0-blues-56
Tomi Engdahl says:
IE#80: 10/100 Base-T Ethernet isolation transformer teardown! (TS8121C)
https://www.youtube.com/watch?v=zJWzdOGM_JM
Blossoms showflat says:
I read that Post and got it fine and informative. Please share more like that…
CanningHill Piers says:
I will really appreciate the writer’s choice for choosing this excellent article appropriate to my matter.Here is deep description about the article matter which helped me more.
Forett Showflat says:
Very useful post. This is my first time i visit here. I found so many interesting stuff in your blog especially its discussion. Really its great article. Keep it up.