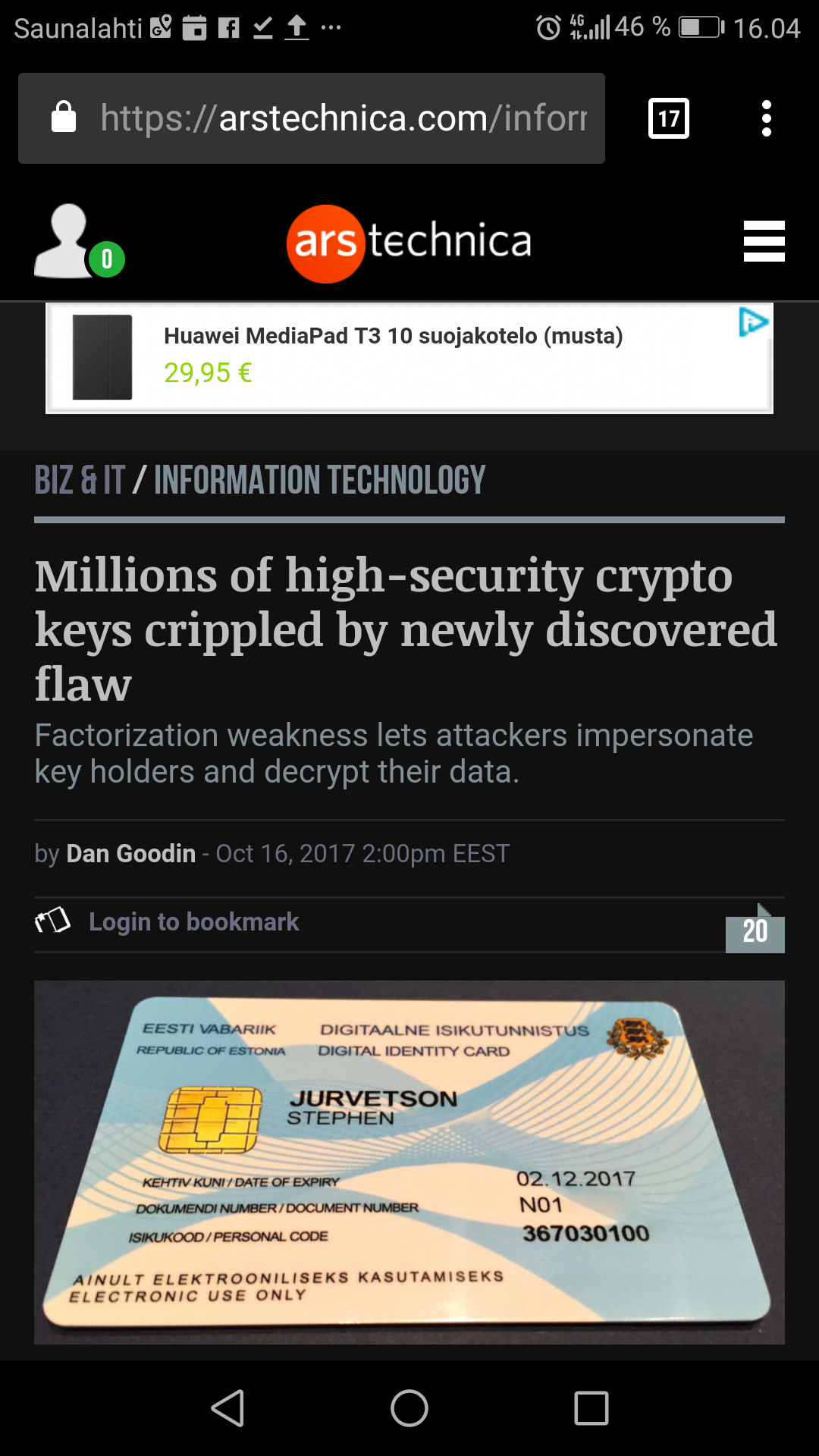
A crippling flaw in a widely used code library has fatally undermined the security of millions of encryption keys used in some of the highest-stakes settings, including national identity cards, software- and application-signing, and trusted platform modules protecting government and corporate computers. The weakness allows attackers to calculate the private portion of any vulnerable key using nothing more than the corresponding public portion.
The flaw is the one Estonia’s government obliquely referred to last month when it warned that 750,000 digital IDs issued since 2014 were vulnerable to attack. Last week, Microsoft, Google, and Infineon all warned how the weakness can impair the protections built into TPM products.
1 Comment
Tomi Engdahl says:
Forget KRACK Attack, 5 Year Old Encryption Bug Returns For Google And Microsoft
https://fossbytes.com/roca-encryption-bug-infineon-chips/
While we were still finding it difficult to forget the Krack attack, a five-year-old bug has resurfaced in a new form to haunt Google and Microsoft. Known as ROCA (Return of Coppersmith’s Attack), the encryption key-related exploit is named after the Coppersmith’s attack.
The range of affected devices – released as early as – includes a large number of Chromebooks, and Windows laptops manufactured by Fujitsu, HP, and Lenovo which feature the hardware chips created by Infineon.
“The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable,”
Researchers calculated the cost of performing the attack via Amazon cloud servers. It would require around $76 to crack a 1024-bit key while more funds would be needed for a 2048-bit key.
Jake Williams, an ex-NSA staffer and the owner of the cybersecurity company RenditionSec, calls ROCA issue more severe than KRACK, Forbes reports. Williams suggests two ROCA attack scenarios; one involves the attacker compromising the digital signature certificate used to validate a software’s source. An attack can use the published public key to reverse engineer the private key to sign the software and impersonate the victim.
Second, the attacker can run malicious code by fooling the Trusted Platform Module (TPM) chip which stores the RSA encryption keys.
The TPM is used to ensure the code used to boot the kernel is valid.
The vulnerability was first spotted in January this year, and Infineon was notified in February. The researcher had an agreement to wait for 8 months before making it public. Software updates and mitigation guidelines have been released by Microsoft, Google, HP Lenovo, Fujitsu. Researchers have provided detection tools to check whether the keys are vulnerable.