I wrote a technical article on embedded systems and IoT security to Uusiteknologia.fi magazine:
Designing modern electronics+ information security
With the latest smart electronics and embedded microprocessors, devices connected to the network can be implemented even better, but even better care must be taken of their data security and protections.
This Designing modern electronics article gives information for the information security protection of modern electronics. Embedded systems are prone to various information security risks, which in the worst case can cause serious consequences for both users and the environment.
That is why information security should be taken into account from the outset, from the design phase of the device or system to the maintenance phase and decommissioning at the end of the solution’s life cycle.
An insecure Internet of Things can pose a significant risk to the entire digital operating environment. And since the Internet is already ubiquitous, every IoT device is vulnerable to attack.
Although the goal should always be to achieve sustainable security, information security operations must be functional already when the product leaves the factory and must be maintained with software updates.
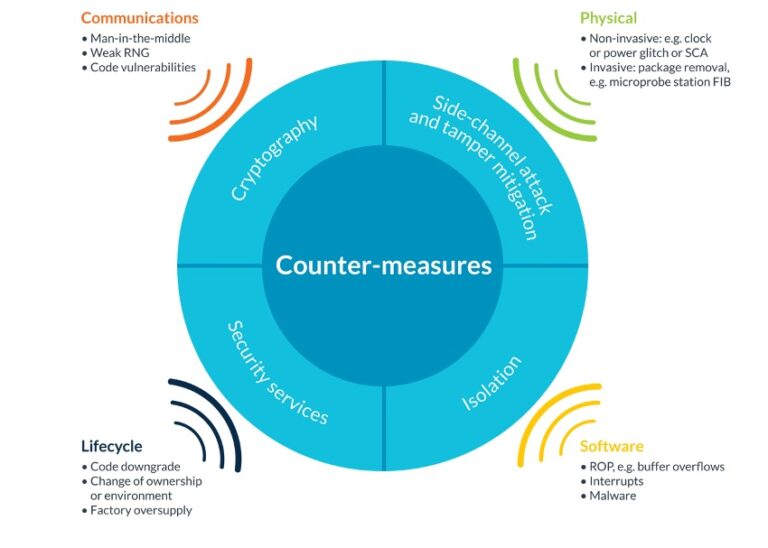
Designers of embedded systems must adopt a security-first approach to ensure that the systems they design are protected from security risks. Therefore, network security, software security and physical security are important in IoT devices.
This article has provided a basic understanding of information security in embedded systems and provides a guide for designers to create reliable and secure systems that are safe for both users and the environment.
Here you can my article in Finnish:
Nykyelektroniikan suunnittelukoulu Plus, osa 5: Sulautettujen ja IoT-ratkaisujen tietoturva
https://www.uusiteknologia.fi/2023/11/08/nykyelektroniikan-suunnittelukoulu-plus-osa-5-sulautettujen-ja-iotn-tietoturva/
If you want to get idea of the article content in English, try Google translation of the article.
37 Comments
Tomi Engdahl says:
Onko älylaitteiden tietoturva kunnossa? “Sähkökatkokin voi olla kyberturvauhka”
https://www.kotitalolehti.fi/alylaitteiden-tietoturva/
Tomi Engdahl says:
The next step is to secure your edge devices, which are often the most vulnerable and exposed to cyber attacks. You need to apply the principle of least privilege, which means granting only the minimum access and permissions necessary for each device to perform its function. You also need to encrypt your data at rest and in transit, using strong and updated algorithms and protocols. Additionally, you need to implement authentication and authorization mechanisms, such as passwords, certificates, or tokens, to verify the identity and legitimacy of your devices.
Tomi Engdahl says:
You need to align your policies with your business objectives, regulatory requirements, and industry standards, such as the NIST Cybersecurity Framework, the ISO/IEC 27000 series, or the Cloud Security Alliance Edge Computing Security Framework. You also need to communicate and enforce your policies across your organization, and review and revise them regularly to reflect any changes or improvements.
Tomi Engdahl says:
Mikä radiolaitedirektiivi? Täältä näet päivitetyt tiedot
https://etn.fi/index.php/13-news/15511-mikae-radiolaitedirektiivi-taeaeltae-naeet-paeivitetyt-tiedot
Elokuussa 2025 tulee EU:n alueella voimaan uusi radiolaitteita koskeva kyberturvadirektiivi.
Tuleva radiolaitedirektiivi tarkoittaa käytännössä, että kaikki EU:n alueella myyntiin elokuun 1 päivän jälkeen vuonna 2025 tulevat langattomat IoT-laitteet täytyy suunnitella ja hyväksyttää uudelleen.
Nykytilanne muuttuu siis 1.8.2025. Sen jälkeen vanhaa, markkinoille aiemmin tuotua laitetta ei voi enää myydä. Kun laite tuodaan saataville EU:n markkinoilla, sen pitää vastata nyt draftivaiheessa olevan RED-direktiivin vaatimuksiin.
Vaatimukset määräävät, että radiolaite ei saa vahingoittaa verkkoa väärinkäyttämällä veron resursseja, mikä johtaisi verkon palvelutason alenemiseen. Radiolaitteessa pitää toteuttaa turvamekanismit, jotta laitteen käyttäjän henkilökohtainen data ja käyttäjän yksityisyys eivät vaarannu. Lisäksi laitteen pitää tukea ominaisuuksia, jotka estävät sen käytön petoksissa.
Etteplanin kyberturva-asiantuntija Antti Tolvanen kertoo seikkaperäisesti esityksessään sekä RED-direktiivistä, että muista EU:n kyberturvahankkeista. Esitys löytyy täältä.
EU ei luonnollisesti ole hakemassa vanhoja langattomia IoT-laitteita kenenkään kotoa, mutta itse asiassa sekin olisi mahdollista. Direktiivin 7. artikla nimittäin sanoo, että mikäli laite asettaa verkon riskin alaiseksi eikä vastaa direktiivin vaatimuksia, kansallinen viranomainen voisi estää niiden käytön.
Webinar: Cyber Security Regulations Update 2023
https://www.youtube.com/watch?v=JgoVLsvDj9E
Tomi Engdahl says:
The Connectivity Standards Alliance has announced the release of the Internet of Things Device Security Specification 1.0 — with a Product Security Verified Mark for IoT devices passing its requirements.
The CSA’s IoT Device Security Specification Promises Better Security, More Transparency
New specification and product mark look to restore consumer confidence in the security of IoT products and services worldwide.
https://www.hackster.io/news/the-csa-s-iot-device-security-specification-promises-better-security-more-transparency-42c5b3a6bfd9?fbclid=IwAR3GkElK8HwDrhOGkSeDCGY-gVXbGqkM1AZ4Sbc_iBmUcQgohFuGmo9gJ8g
Tomi Engdahl says:
SPDL (Secure Product Development Lifecycle) comes into play. SPDL is a comprehensive framework that provides guidance and structure for developing and maintaining secure products. According to the widely adopted IEC 62443-4-1 standard, it consists of eight essential practices that cover every stage of the product lifecycle.
https://www.etteplan.com/about-us/insights/secure-product-development-lifecycle-essential-tool-for-product-development/
Tomi Engdahl says:
When manufacturing IoT devices with embedded systems, it’s helpful to consider broader IoT security standards, like EN 303 645 and IEC 62443-4-2, as well as the NIST Cybersecurity for IoT Program, NISTIR 8259A: Core Device Cybersecurity Capability Baseline. Additionally, for those products intended for European customers, manufacturers must show proof that their products meet the EU’s regulations, such as the General Data Protection Regulation (GDPR) and the EU Cybersecurity Act, in addition to Radio Equipment Directive (RED), regulations for medical devices (MDR), and in vitro diagnostic medical devices (IVDR) and NIS2 Directive, depending on the use case.
https://www.thefastmode.com/expert-opinion/33730-vulnerabilities-in-embedded-systems-and-the-evolving-cybersecurity-regulations-landscape
Tomi Engdahl says:
IEC 62443-4-2 standardin hyödyt ja haasteet yritykselle : systemaattinen kirjallisuuskatsaus
https://jyx.jyu.fi/handle/123456789/92255
Tomi Engdahl says:
https://kpmg.com/fi/fi/home/Pinnalla/2024/01/nis2-varmista-tietoturvasi-vaatimustenmukaisuus.html?gad_source=1&gclid=CjwKCAjwoPOwBhAeEiwAJuXRh_cjuQgaNF934Ceib9A3Kk_5G3qk-GTzXkaUOpcEo3gG1yH6E9CKExoCXEIQAvD_BwE
Tomi Engdahl says:
https://www.dnv.fi/services/iso-iec-27001-tietoturvallisuuden-hallintajarjestelma-3327?gad_source=1&gclid=CjwKCAjwoPOwBhAeEiwAJuXRh28q2lBs1g86qc9osTo_iMCjodSLDGrrp0z-4-KHw4HQOEpSbGqfuxoCnP4QAvD_BwE
Tomi Engdahl says:
https://huld.io/fi/blogi/radiolaitedirektiivi-red-paivittyy-lue-kaikki-mita-sinun-tulee-tietaa/
Tomi Engdahl says:
https://www.kyberturvallisuuskeskus.fi/sites/default/files/media/publication/Ohjelmistoturvallisuuden%20tila%202023.pdf
Tomi Engdahl says:
Toimialat, joita direktiivi koskee
Direktiivi koskee automaattisesti kaikkia keskisuuria (50+ henkilöä ja yli 10 milj. liikevaihto) ja suuria yrityksiä, jotka toimivat kriittisillä toimialoilla. Direktiivi koskee myös kaikkia kansallisesti kriittiseksi toimijoiksi määriteltyjä koosta riippumatta
https://www.loihdetrust.com/nis2-direktiivi/
Tomi Engdahl says:
IoT Security
MITRE EMB3D Threat Model Officially Released
https://www.securityweek.com/mitre-emb3d-threat-model-officially-released/
MITRE announced the public availability of the EMB3D threat model for embedded devices used in critical infrastructure.
MITRE, the non-profit technology and R&D company, on Monday announced the public availability of its EMB3D threat model for embedded devices used in critical infrastructure and other industries.
EMB3D was developed by MITRE in collaboration with cybersecurity and industrial sector partners such as Red Balloon Security, Narf Industries, and Niyo ‘Little Thunder’ Pearson of ONE Gas.
Unveiled in December 2023, the framework provides a knowledge base of cyber threats to embedded devices used in the critical infrastructure, IoT, healthcare, automotive, and manufacturing sectors.
The resource is recommended for vendors, asset owners and operators, testing organizations and cybersecurity researchers.
The MITRE EMB3D™ Threat Model
https://emb3d.mitre.org/
The EMB3D Threat Model provides a cultivated knowledge base of cyber threats to embedded devices, providing a common understanding of these threats with security mechanisms to mitigate them.
This initial release of EMB3D includes the Device Properties and Threats enumerations. The full set of Mitigations will be available in the Summer 2024 update.
What is EMB3D™
EMB3D is a threat model for embedded devices found in industries such as critical infrastructure, Internet of Things, automotive, healthcare, manufacturing, and many more. The threat model is intended to be a resource to help vendors, asset owners/operators, test organizations, and security researchers to improve the overall security of embedded devices’ hardware and software. This threat model aims to serve as a central repository of information, defining known threats to embedded devices and their unique device features/properties that enable specific threat actions. By mapping the threats to the associated device features/properties, the the user can easily enumerate threat exposure based on the known device features.
Tomi Engdahl says:
My new articles:
Information security requirements are increasing
https://www.convergens.fi/post/information-security-requirements-are-increasing
Tietoturvavaatimukset kasvavat
https://www.convergens.fi/fi/post/tietoturvavaatimukset-kasvavat
Tomi Engdahl says:
Standards are needed in cyber security
https://www.convergens.fi/post/standards-are-needed-in-cyber-security
Kyberturvallisuudessa tarvitaan standardeja
https://www.convergens.fi/fi/post/kyberturvallisuudessa-tarvitaan-standardeja
Tomi Engdahl says:
https://www.cisa.gov/resources-tools/resources/product-security-bad-practices
Tomi Engdahl says:
https://www.edn.com/understand-the-hardware-dependencies-of-iot-security/
Tomi Engdahl says:
https://etn.fi/index.php/13-news/16721-sopimusvalmistus-esillae-tallinnassa-uusi-regulaatio-aiheuttaa-uusia-haasteita
Tomi Engdahl says:
https://www.zdnet.com/article/are-all-linux-vendor-kernels-insecure-a-new-study-says-yes-but-theres-a-fix/
Tomi Engdahl says:
https://etn.fi/index.php/working-on-your-site/13-news/14619-kiinnostaako-sulautettujen-tietoturva-nyt-voit-lukea-siitae-e-kirjan
Tomi Engdahl says:
https://www.arrow.com/en/research-and-events/articles/security-solutions-ebook?utm_source=Social&utm_medium=PaidSocial&utm_term=SecurityeBookSupplierPromotion-BuyersEngineers-BrandEMEA&utm_content=1×1-SS-English-122222&utm_campaign=Arrow-Global-Arrow-SecurityeBook
Tomi Engdahl says:
https://emb3d.mitre.org/
Tomi Engdahl says:
https://etn.fi/index.php/72-ecf/16735-ecf24-suurin-osa-laitteista-ja-ohjelmistoista-muuttuu-laittomiksi
Tomi Engdahl says:
https://www.clydeco.com/en/insights/2024/04/the-eu-s-new-product-liability-directive
Tomi Engdahl says:
ECF24 presentation by Antti Tolvanen, Etteplan – Maria01 – September 26, 2024, Helsinki
https://www.youtube.com/watch?v=42MhkCv_TUc
NIS2, RED, CRA, AI Act and Data Act –
How will EU regulatory changes affect design and maintenance of embedded products
Tomi Engdahl says:
https://www.cov.com/en/news-and-insights/insights/2024/10/what-can-you-expect-from-the-new-product-liability-directive#layout=card&numberOfResults=12
Tomi Engdahl says:
https://www.eu-data-act.com/
Tomi Engdahl says:
https://www.uusiteknologia.fi/2024/10/22/nis2-direktiivin-noudattamiseen-10-toimenpidetta/
Tomi Engdahl says:
https://www.uusiteknologia.fi/nykyelektroniikan-suunnittelukoulu-1-3-osaa/
Tomi Engdahl says:
https://etn.fi/images/ecf/ecf24-presentations/Etteplan_regulations_ECF_2692024.pdf
Tomi Engdahl says:
All you need to know to ensure NIS2 compliance
https://secomea.com/guides/mastering-nis2-compliance/
Tomi Engdahl says:
Nis2-direktiivin määräaika umpeutui, Suomi myöhästyi
Aleksi Kolehmainen18.12.202422:10KyberTietoturva
Uusi nis2-direktiivi asettaa tiukemmat vaatimukset monille organisaatioille ja antaa viranomaisille mahdollisuuden määrätä jopa miljoonien eurojen sakkoja. Hallituksen lakiesitys direktiivin panemiseksi täytäntöön on jumissa eduskunnassa.
https://www.tivi.fi/uutiset/nis2-direktiivin-maaraaika-umpeutui-suomi-myohastyi/7fab3ae4-de76-457f-9522-19045436e658
Tomi Engdahl says:
The ‘S’ in IoT stands for security.
The ‘P’ in AI stands for privacy.
Tomi Engdahl says:
https://www.edn.com/the-future-of-cybersecurity-and-the-living-label/
Tomi Engdahl says:
https://hackaday.com/2025/04/03/mit-wants-you-to-secure-your-hardware-designs/
Tomi Engdahl says:
Simplify European Cyber Resilience Act compliance. Learn more at http://www.infineon.com/eu-cra.
#Infineon #CyberSecurity #EUCRA